The Microsoft 365 governance tool for clarity and control
Do you know who has access to what in Microsoft 365?
ShareGate Protect gives you the clarity to see what’s happening, the tools to fix what’s risky, and the insights to keep improving.
.avif)
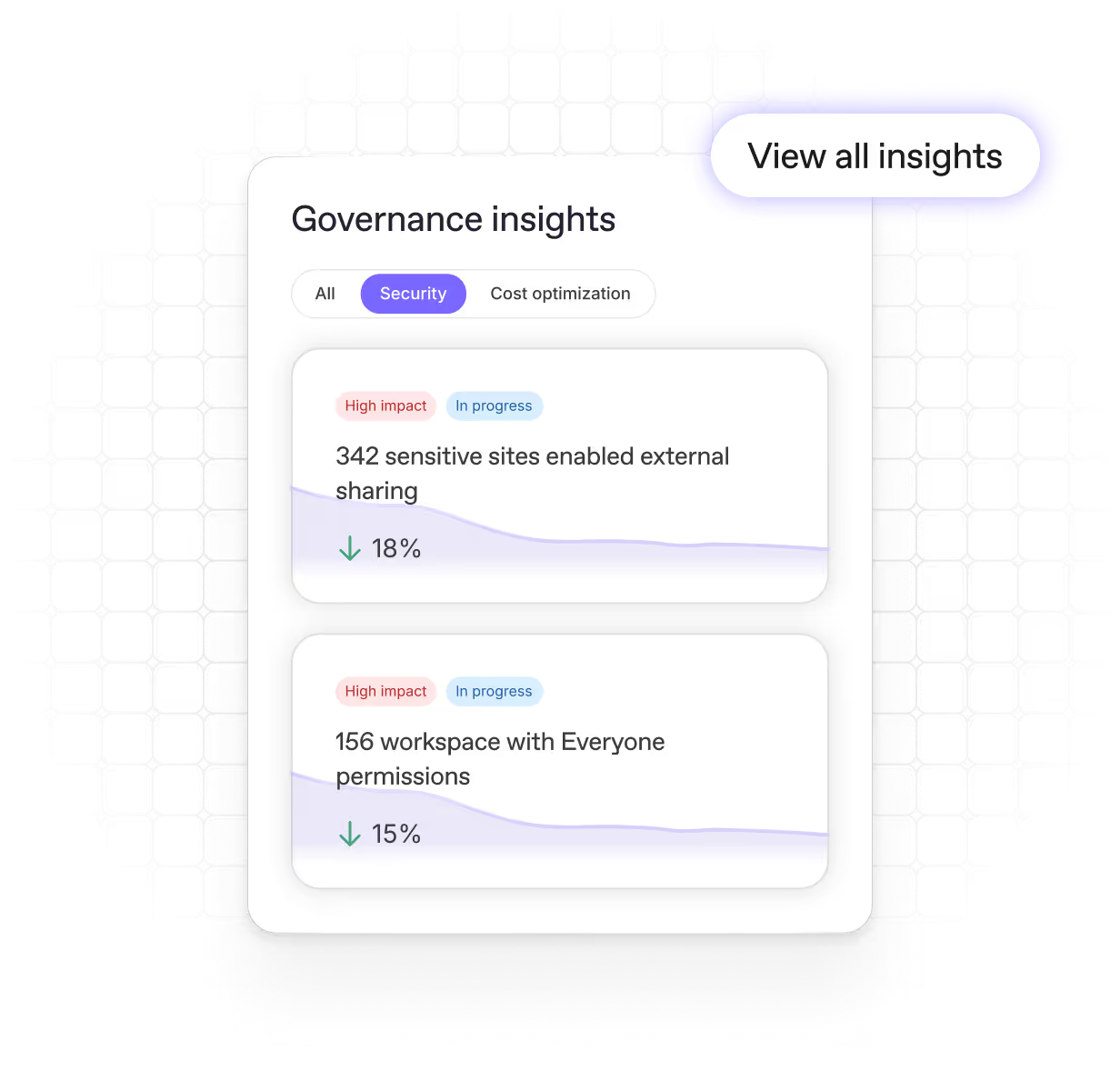
Assess your tenant in minutes
Get a unified, clear view of your tenant to see what matters most and spot issues fast.
.avif)
Take action right where you find the problem
Fix permissions, clean up inactive workspaces, and keep collaboration running smoothly, all from one space.
.avif)
Govern smarter, not harder
Use clear, insights and smart recommendations to refine policies and keep improving your governance with confidence.
Trusted by 100,000+ IT pros
Conquer every Microsoft 365 governance challenge
Whether you’re tackling oversharing, tenant sprawl, or Copilot readiness, ShareGate Protect helps you reduce risk, prove control, and keep governance from becoming unmanageable.
See who has access to what in Microsoft 365
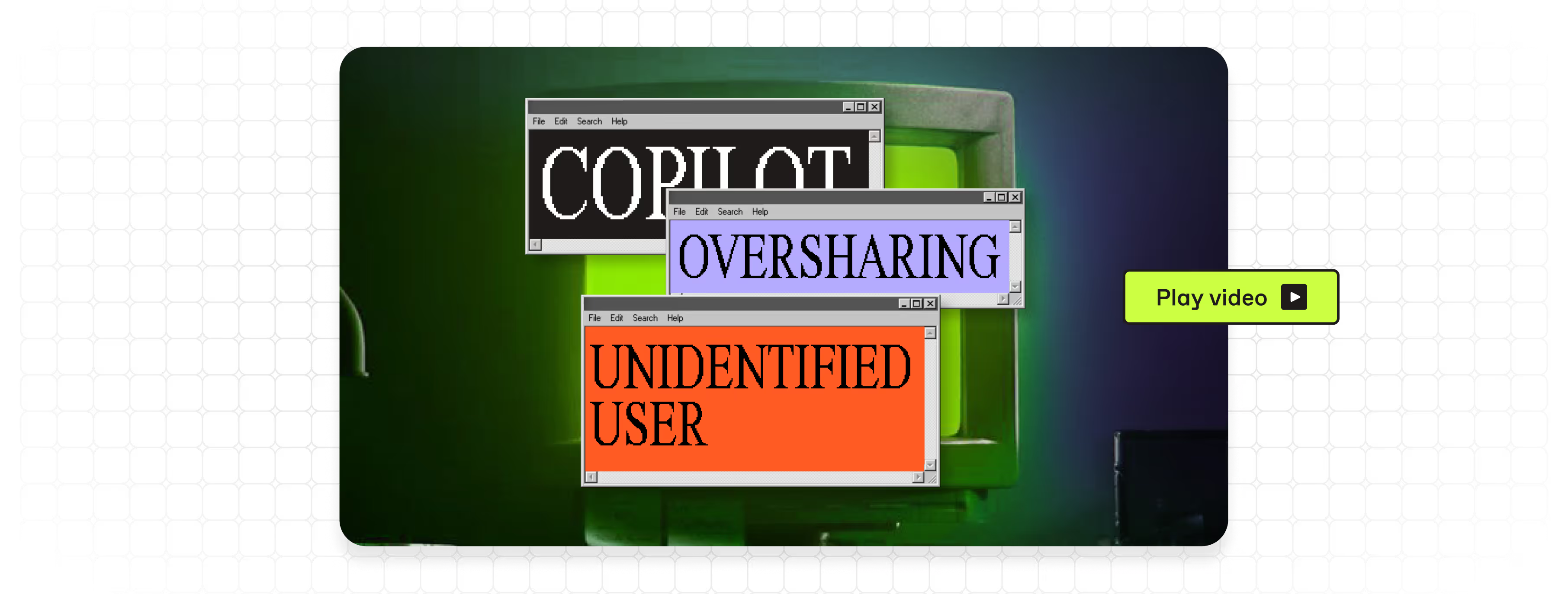
Find and fix risky sharing across Teams, SharePoint, Groups, and OneDrive.
Stay ahead of
Microsoft 365 AI security risks
See what Copilot can access and manage permissions to protect access to your sensitive data.
.avif)
Eliminate unnecessary costs
Find inactive teams, unused sites, and wasted storage, then clean them up safely to reduce cost and governance overhead.
“Time is money. Because we don’t have to spend as much time keeping the environment tidy, we can do more to help the business.”
– Vera Van Es
Fonctional Microsoft 365 Administrator
.avif)
Get the tools to offer outstanding service for Microsoft 365
The ShareGate Partner Program turns complex Microsoft 365 projects into repeatable business.
- Scope smarter with automated migration and governance assessments
- Stand out with certification and training that prove your expertise
- Get support anytime with 24/7 access and roadmap influence
- Grow faster through co-marketing and lead sharing

Real humans, real fast.
Choosing ShareGate means choosing a highly qualified team of tech support. We’re always there for you.
Know what to expect from your ShareGate experience








.avif)
