Prevent data leaks in Microsoft Teams with Purview DLP

Table of contents
Microsoft MVP Jasper Oosterveld delves into Microsoft Purview Data Loss Prevention, sharing insights on combining it with Microsoft Purview Information Protection and recommendations for implementation.
Although Microsoft Teams has a default authentication and authorization process to protect your data, there’s still a chance that your organization's data could be exposed to internal and external users who gain access.
It’s a cause for concern as it could lead to unauthorized access and data leaks.
In a previous article, I talked about how Microsoft Purview Information Protection helps to protect sensitive data in Teams. Another solution that can help prevent data from falling into the wrong hands is Microsoft Purview Data Loss Prevention (DLP).
Let’s dive in!
What is Microsoft Purview Data Loss Prevention?
Microsoft Purview Data Loss Prevention is a solution that helps to prevent the unsafe or unauthorized sharing, transfer, or use of sensitive data in your organization.
Using it, you can identify and monitor sensitive data, which allows your organization to enforce your data protection policies and keep your information safe, and ensure regulatory compliance with standards such as HIPAA and GDPR.
Microsoft Purview DLP is a unified solution with a wide scope, not only focusing on Microsoft 365 but also allowing your organization to protect your sensitive data within the following locations:
- Microsoft 365 services: Microsoft Teams, Exchange, SharePoint, and OneDrive.
- Devices: Audit and manage activities employees perform on sensitive items physically stored on Windows 10, Windows 11, or macOS devices.
- Instances: Monitor, detect, and take actions when sensitive items are used and shared via non-Microsoft cloud apps.
- On-premises repositories: Apply DLP policies on locally stored data.
- Fabric and Power BI workspaces: Detect the upload of sensitive data to a dataset within Fabric and Power BI.
- Copilot (Preview): Block the processing of documents with a specific sensitivity labels for prompts.
The focus of this article revolves around Microsoft 365 apps, particularly around working with documents and chatting in Teams. If you've already implemented Microsoft Purview DLP for Microsoft 365 services, I recommend taking it a step further and looking into Endpoint DLP.
For even more enhanced security, the Microsoft Compliance Center ensures IT admins leverage the comprehensive tools available to ensure data security and meet industry standards effectively.
Ensure your organization has the proper licensing for Microsoft Purview DLP
To unlock the full power of Microsoft Purview DLP, you need to ensure your business users have the proper licenses. So, to use DLP for Exchange Online, SharePoint Online, and OneDrive for Business1, one of these licenses is necessary:
- Microsoft 365 E5/A5/G5/E3/A3/G3, Microsoft 365 Business Premium, SharePoint Online Plan 2, OneDrive for Business (Plan 2), Exchange Online Plan 2
- Office 365 E5/A5/G5/E3/A3/G3
- Microsoft 365 E5/A5/G5/F5 Compliance and F5 Security & Compliance
- Microsoft 365 E5/A5/F5/G5 Information Protection and Governance
It's worth noting that the licensing structure for Teams is a bit different. So, to use DLP for Teams, you'll need to have one of the following licenses:
- Microsoft 365 E5/A5/G5
- Microsoft 365 E5/A5/G5/F5 Compliance and F5 Security & Compliance
- Microsoft 365 E5/A5/F5/G5 Information Protection and Governance
- Office 365 E5/A5/G5
Microsoft Purview Administration Center
Purview DLP offers unified, flexible policy management and enforcement across devices, apps, and services from the Purview administration center. This is the location where you manage and monitor your Purview DLP solution.
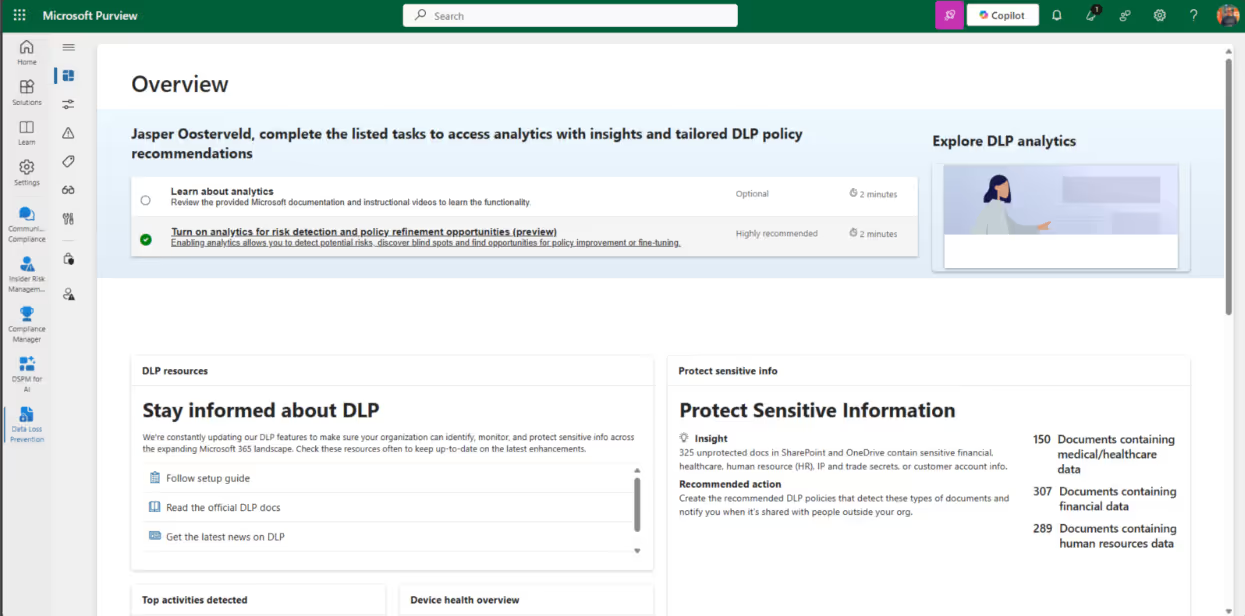
You can start by configuring your first policy:
But before you start configuring, it’s important to review your information protection policy. This policy should outline the regulations or internal processes related to the internal and external access of your sensitive data.
Microsoft offers various pre-defined DLP templates that are tailored to specific countries and regions, such as the US Patriot Act, UK Data Protection Act, or GDPR. These templates come with pre-configured sensitive information types and rules consisting of conditions and actions. You only have to assign the template to one or more Microsoft 365 locations. In my experience with the implementation of DLP for any organization's data, custom policies are often used.
How Microsoft Purview Data Loss Prevention and Microsoft Purview Information Protection can work together
Microsoft Purview DLP compliments Microsoft Purview Information Protection. Together, these services offer a solution for protecting and managing data across your organization.
In a previous article, we talked about the importance of using Purview Information Protection to safeguard sensitive data. Now, with Purview DLP, you can identify and monitor sensitive data right from the get-go. This allows your organization to enforce your data protection policies and keep your information safe.
Use case for combining both services
One use case for combining both services is to provide an extra layer of protection for your organization's data.
Let’s say you have some intellectual property (IP) that you can’t share outside of your organization. With Microsoft Purview DLP, you can detect if your IP is being shared externally, either by a dedicated sensitive information type or a sensitivity label that’s attached to the IP.
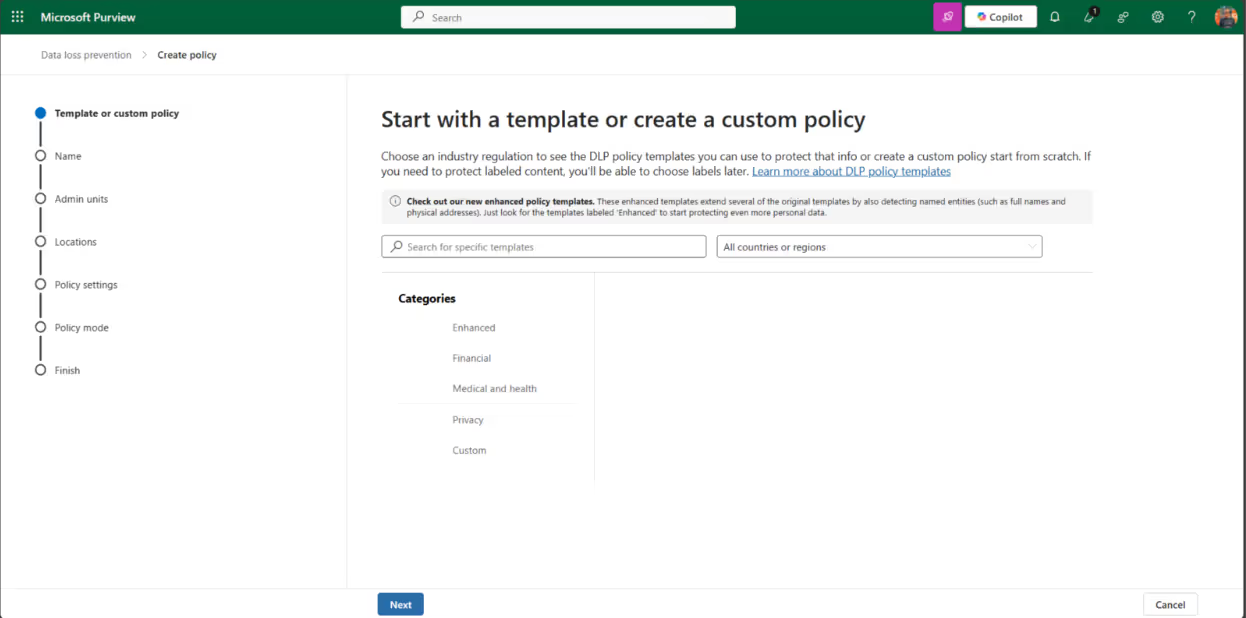
To make the Microsoft Purview DLP service and the Microsoft Purview Information Protection service work together, you can configure a rule within a Purview DLP policy:
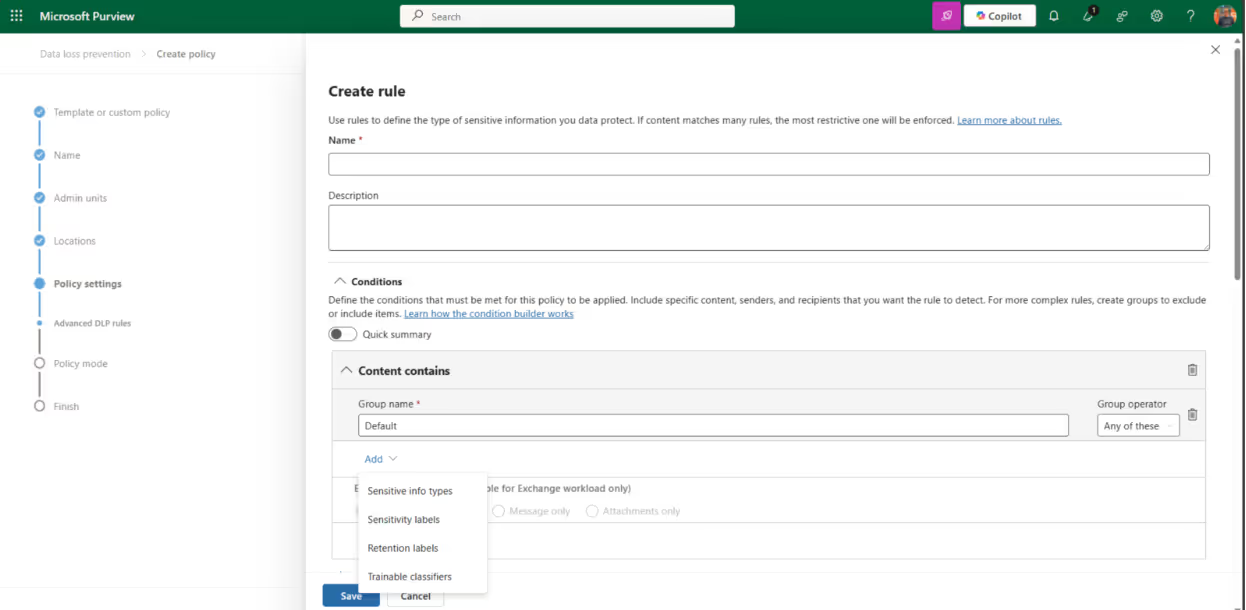
You can trigger the condition of your policy based on your sensitive information type or a sensitivity label. The sensitivity label option is only available for the following locations applied within your policy:
- Exchange Online email messages
- SharePoint Online
- OneDrive for Business sites
- Windows 10/11 devices
That means you’ll need to create an additional Purview DLP policy for chat and channel messages in Microsoft Teams.
Exploring the end-user experience of Microsoft Purview Data Loss Prevention
We talked about the configuration and importance of Microsoft Purview DLP. Now, let’s shift our focus to your users’ experience with it. This is an important aspect to consider because it'll help you shape your adoption and change management strategy.
Your business users might have questions such as:
- Why is it important for our organization?
- What is the impact on my work?
- Where can I find more information in case I have any questions?
- What is expected from me as an employee?
Before you start implementing Purview DLP, it's essential to address these questions.
Now, to give you an idea of the user experience with Purview DLP, let's take a look at how the tool works for:
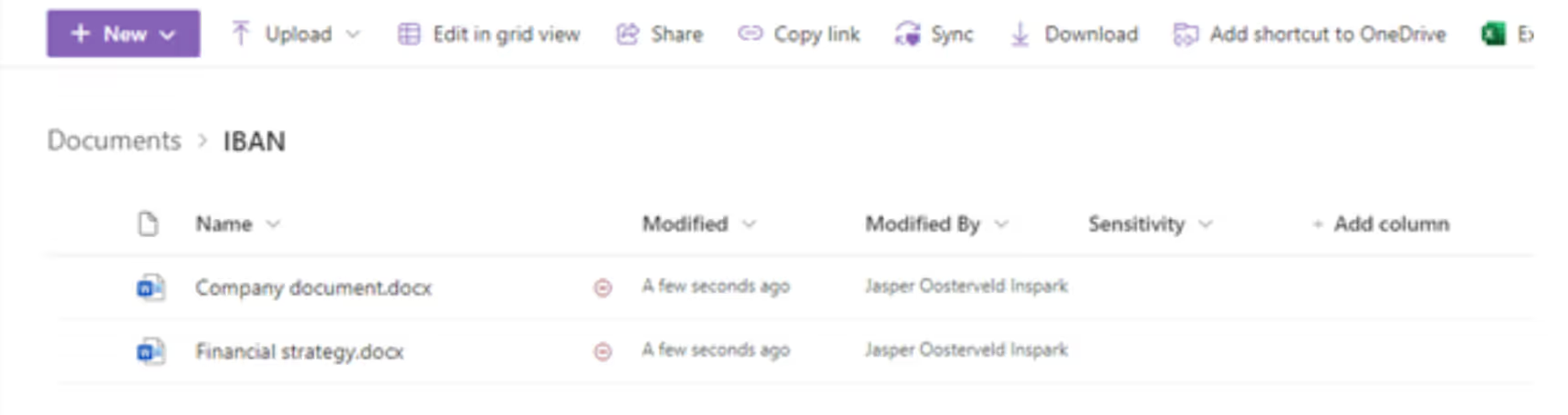
Files (SharePoint)
In this example, we are detecting files and chats containing IBAN (International Bank Account Number). The files, triggered by the policy, are displayed with a red icon:
The detail page of the files displays a policy tip:
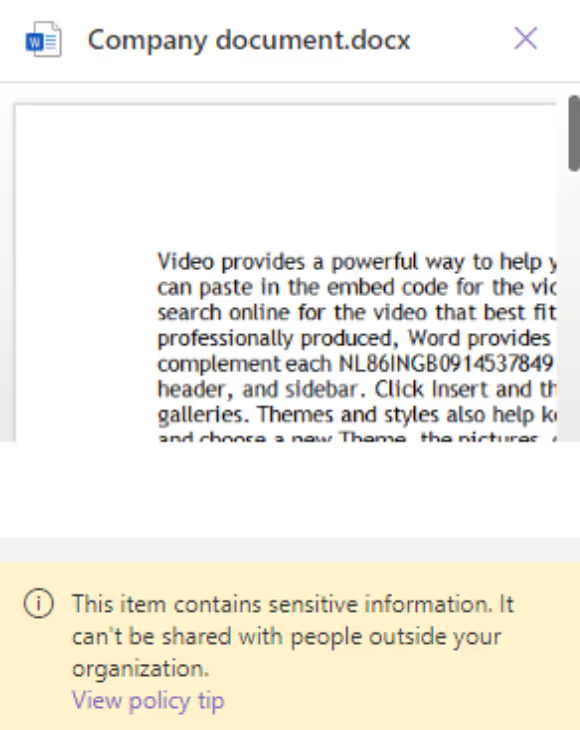
Depending on the configuration of the policy, a user can override or report the triggered policy.
Chat
In this example, we are detecting information about a secret project within the organization called Project MRVN. Once a chat message contains sensitive information related to the project, the policy is triggered:
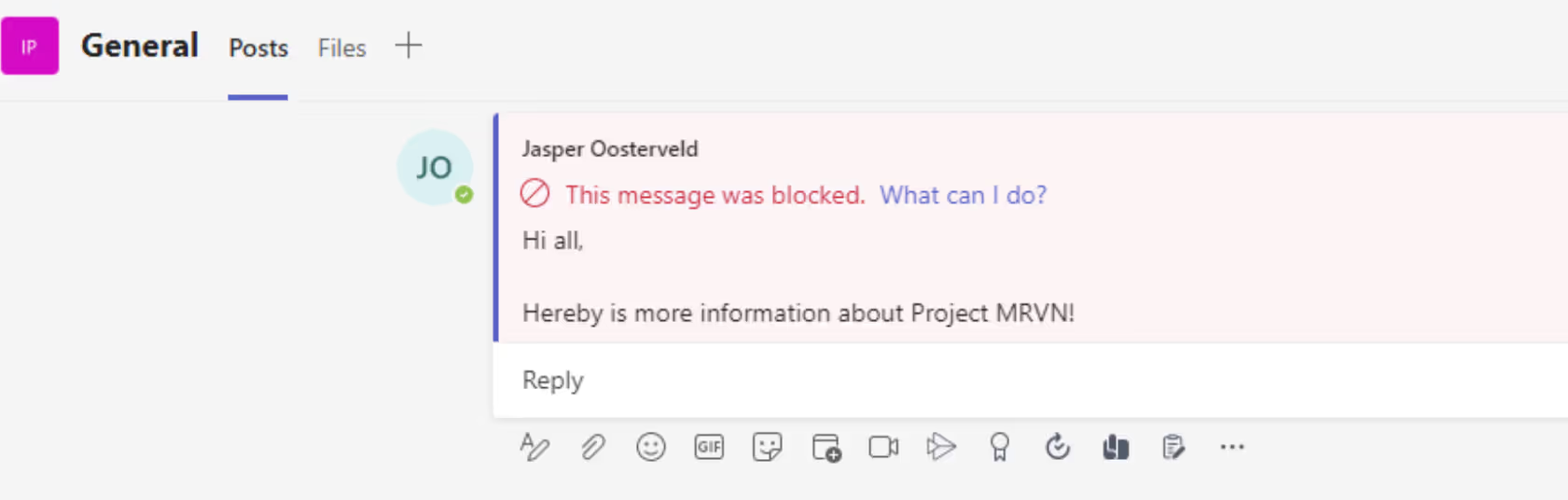
Reporting and alerts
An important stakeholder for your Microsoft Purview DLP implementation is the Chief Information Security Officer (CISO).
When a DLP policy is triggered, it means that sensitive or confidential data may be at risk of being accessed or leaked outside of the organization. Purview offers multiple features to send notifications and assign alerts, allowing your CISO to assess the situation and take appropriate action.
Without these features, your CISO may not be aware of a potential security threat until it’s too late to take effective action, leaving your organization vulnerable to data loss. One of the reporting features is the activity explorer:
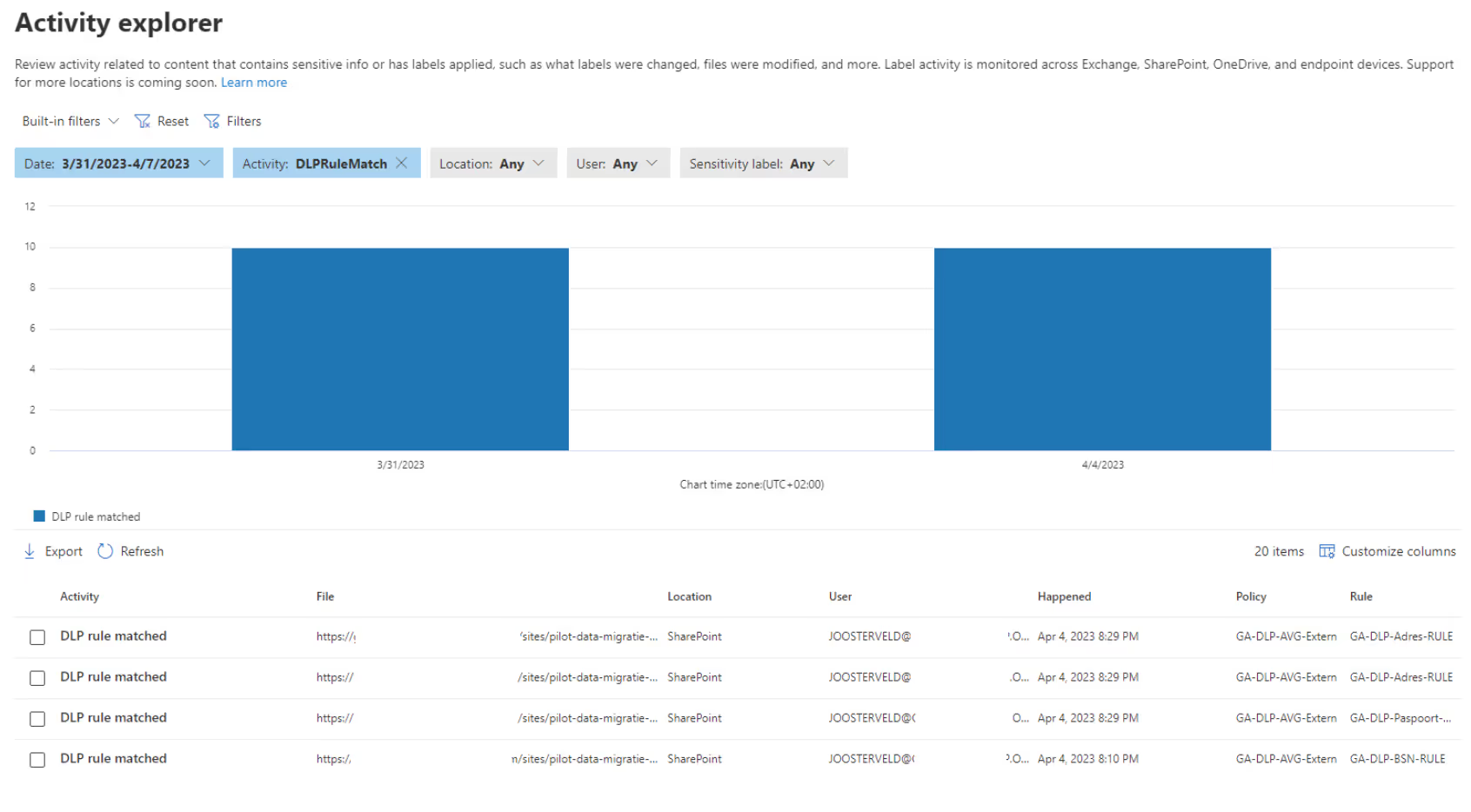
The triggered policies from the last four weeks are displayed and the CISO can view more details per match:
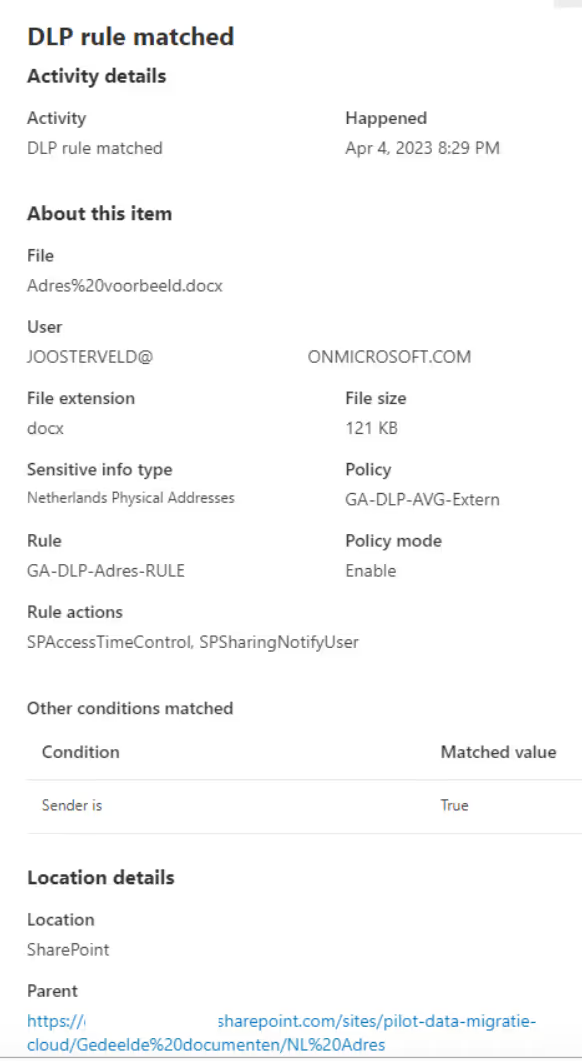
The CISO can contact the corresponding employee and discuss the triggered policy. To view the actual content of the file, your CISO needs access to the content explorer:
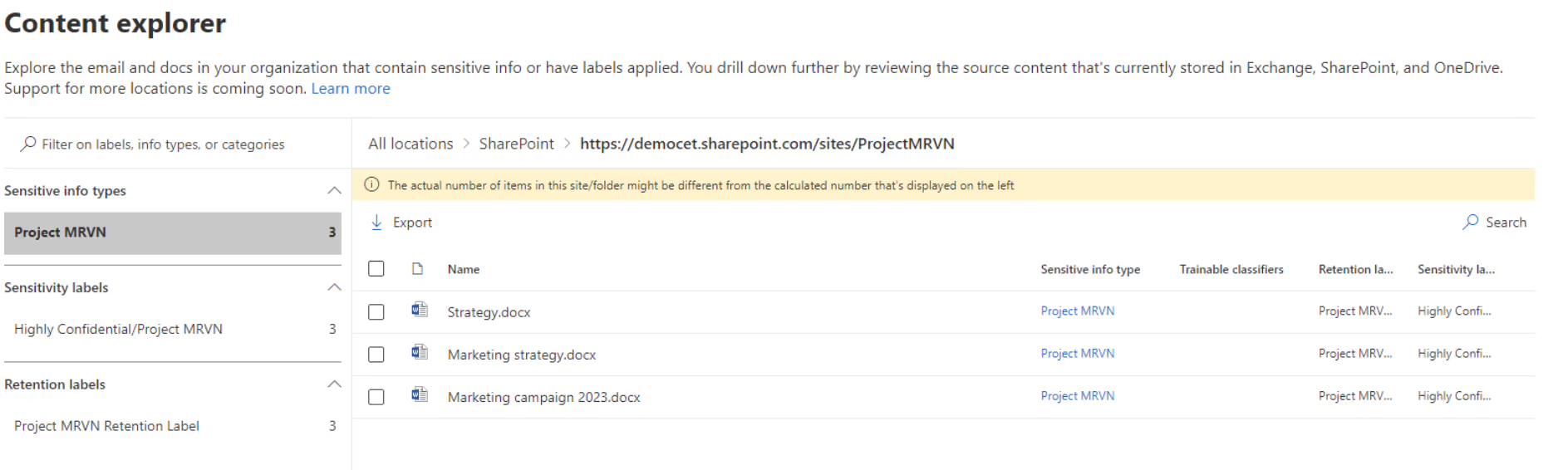
Each file can be investigated for the presence of sensitive information. Heads up: the use of the content explorer needs to be reviewed with your internal privacy policies because it has the potential to reveal private content that belongs to your end users. Therefore, I advise assigning your CISO at least the role of Information Protection Analyst.
Recommendations for successful implementation
I have some recommendations for your Microsoft Purview DLP implementation that I'd like to share with you.
Multiple policies
Your content in Microsoft Teams is divided into the following Microsoft 365 services:
- OneDrive: Shared files from the Teams chat are stored in OneDrive,
- SharePoint: Shared files in a channel from Teams are stored in SharePoint.
- Microsoft Teams: Chat and channel messages from Teams.
Each location comes with its own set of conditions you configure within the set of rules of your policy. However, when combining all locations, not all conditions are available. I mention this in my previous article on Microsoft Purview Information Protection. And often, in combination with Exchange, there’s a bit of a challenge when it comes to policies not working at all. That’s why I suggest dividing the policy between SharePoint and OneDrive and Teams to manage things better.
Testing
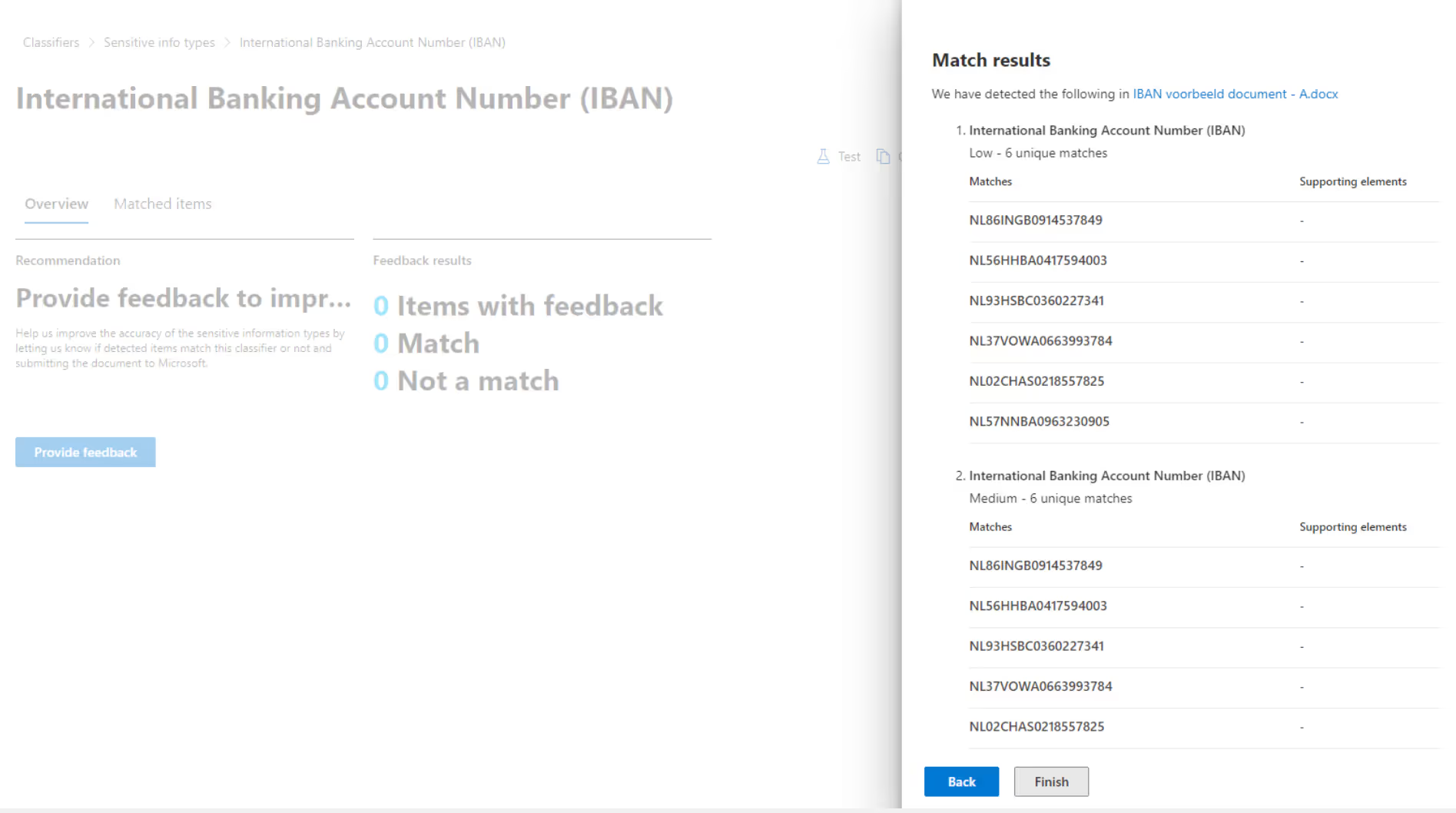
Test your newly created Microsoft Purview DLP policy before you release them into the wild. Here are a couple of ways:
- Gather some example documents containing real content to see if your policies are triggered properly. I recommend using the test option within an out-of-the-box or custom-sensitive information type to run your tests (see screenshot below).
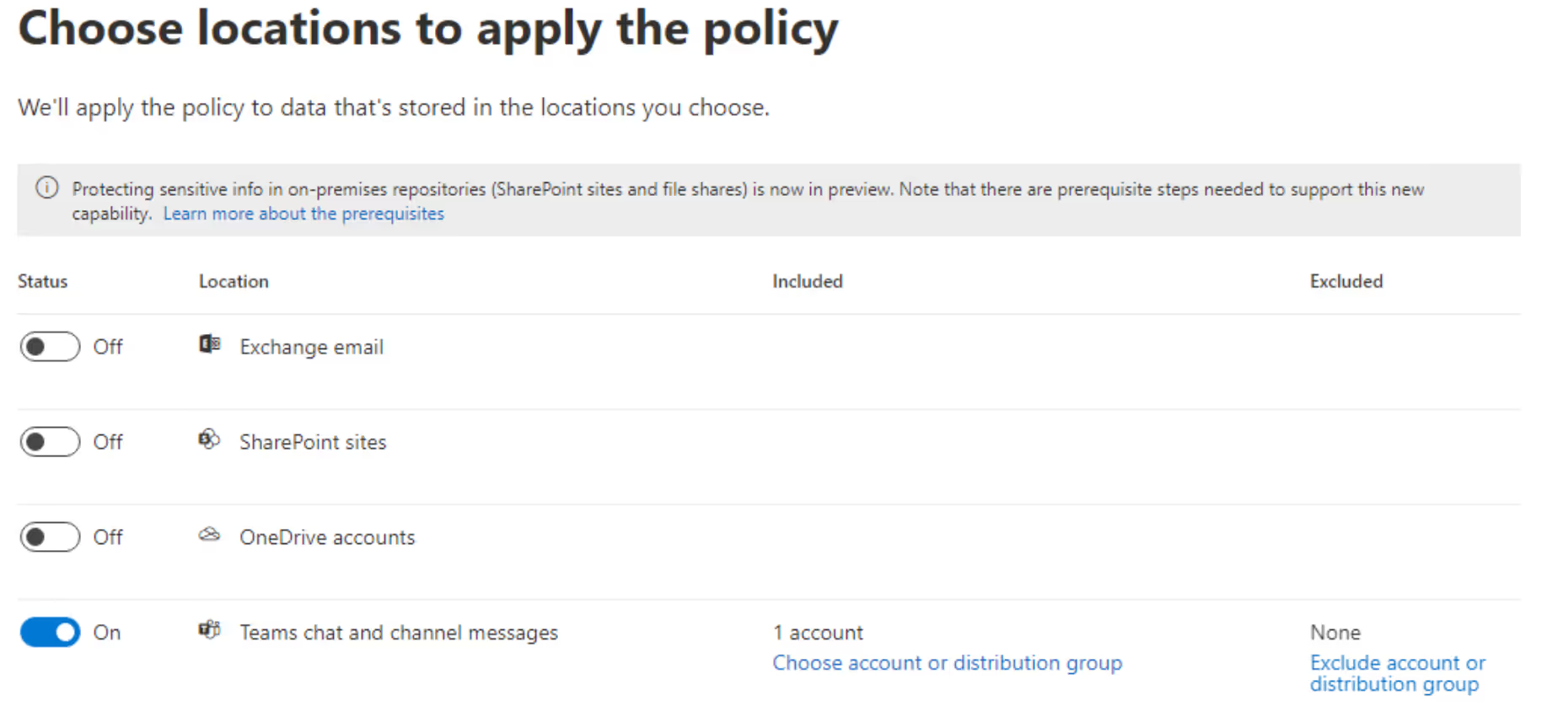
- Another way is to create a test team in Teams and assign the policy to this team. (See screenshot below) You can also create another policy for the connected SharePoint site and OneDrive accounts of the employees who will be participating in the test. To do this, you can use the included and excluded features in the configuration menu of the policy. This will help ensure your policies are effective before releasing them into the wild.
I recommend combining Data Loss Prevention with your Purview Information Protection pilot. This allows you to maintain control and really test the application of DLP, in combination with sensitivity labels, within your department. Once the pilot is successful, you can move on to another department and then gradually roll out Microsoft Purview DLP with Information Protection across your organization.
To sum up, Microsoft Purview DLP is a smart move that can help you avoid financial losses, comply with regulations, maintain customer trust, and keep your organization’s sensitive information secure.


.svg)
.avif)
%20(1).avif)







.avif)


.jpg)
.jpg)
