Define an effective data classification scheme for Microsoft 365
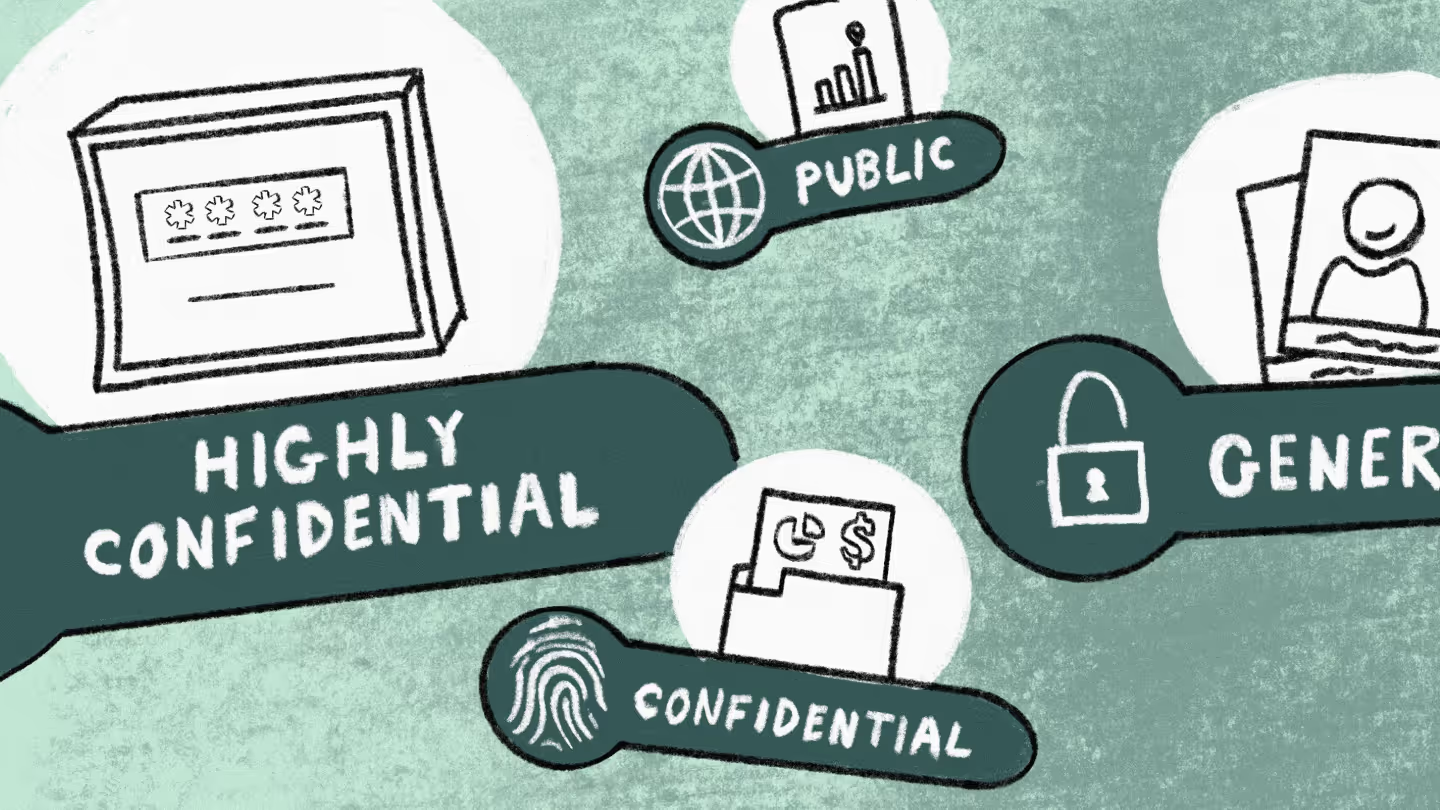
Table of contents
We spoke to Marc D Anderson (@sympmarc), Microsoft MVP and co-founder of Sympraxis Consulting, about how to define an effective data classification scheme that offers a more secure Microsoft 365 deployment.
Related reading for IT: The ultimate guide to Microsoft 365 external sharing
Data classification makes it easier to locate, leverage, and protect your valuable data—and is crucial for effective risk management and compliance.
The thing is, not all data is created equal. You don't need to apply the same controls to the internally-shared lunch menu as you would to a highly confidential spreadsheet with info about quarterly earnings.
In fact, adding unnecessary restrictions can negatively impact user adoption and result in people turning to other, un-approved tools. Classifying your data enables you to manage it according to its value and level of sensitivity instead of treating all data the same.
Many organizations understand the need for data classification and want to implement it, but don't know where to begin. That's why we asked Microsoft MVP Marc D Anderson about best practices, tips, and tricks to help you get started.
What is data classification?
If you've ever used a filing cabinet to keep track of your tax returns, then you're probably familiar with the concept of data classification. Put simply, it's the process of organizing data into categories that make it easier for you to leverage and protect it.
"The implementation is different, but the concepts are the same," Marc D Anderson tells ShareGate. "You don't need to totally rethink everything every time new technology comes along. Most organizations probably have some idea what it is, 'data classification' is just what Microsoft is calling it with this technology."
Categorizing your data in a way that conveys its level of sensitivity helps you better understand where sensitive data lives, what users are doing with it, and why it may be at risk. Once categorized, the appropriate controls can be applied to monitor and control data access, transportation, and storage.
A data classification policy ensures that sensitive information is handled properly with respect to the threat it could pose to your organization.
Data classification scheme
In order to categorize your data, you first need to know what the categories are! That's where a data classification scheme comes in. It maps out and defines all of the available options.
Microsoft's classification scheme is impressive because they've managed to pare it down to just four categories: Highly confidential, Confidential, General, and Public.
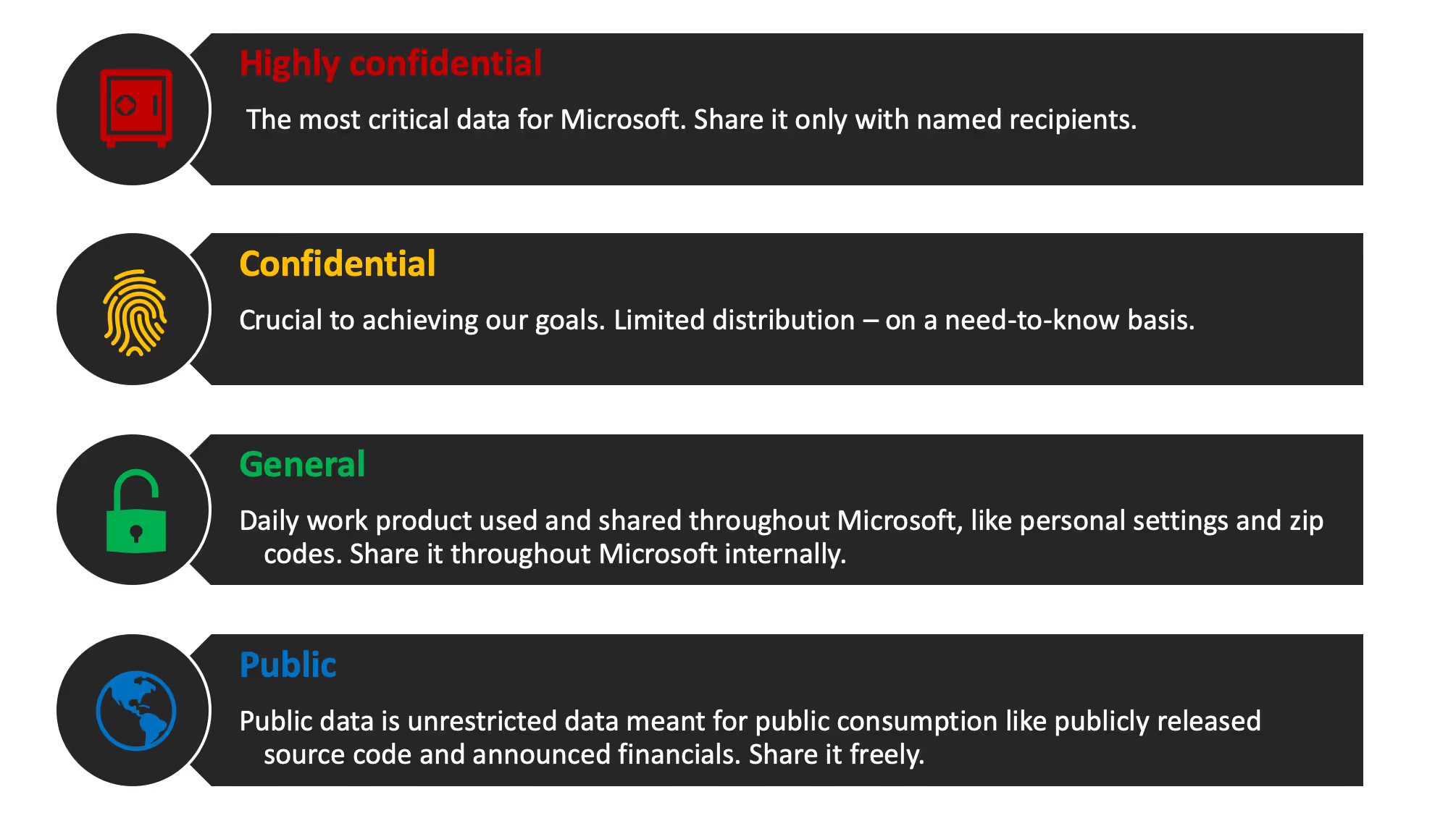
You don't have to make yours the same as Microsoft's—in fact, you're better off creating one that's tailored to the specific needs of your organization. But Microsoft's system is well-considered and there are some great takeaways to consider.
Delve deeper: How to build and apply a data classification and protection policy in Microsoft Purview
Best practices for creating an effective data classification scheme
If you're ready to define your own data classification scheme, the following best practices, advice, and tips can help you get started on the right foot!
#1: Identify your valuable content
Just like all data isn't equal, no two organizations are exactly the same. An online retailer has different security needs than a manufacturer dealing with government contracts.
I think the key is for any organization to actually think about what content they have and what matters to them. Not what Microsoft has demonstrated, not what some consultant has said in a session at a conference. It's about understanding whether or not—and in many cases, it's not—something needs that extra level of protection.
Marc D Anderson, Microsoft MVP
Keep in mind that data classification serves a bigger purpose than just slapping a label on a piece of content. You want to categorize your content so that you can apply policies in a way that makes sense. If you apply a retention policy, that has an effect: you can't delete whatever that policy has been applied to.
I think it's important that people lock things down in a way that makes sense, and not apply one-size-fits-all thinking.
Marc D Anderson, Microsoft MVP
"Sometimes that sort of shocks people," says Anderson. "They go, 'Well, yeah, but I want to delete it.' And it's like 'Well, you said you can't.' So, I think it's very important that people understand how it works for their organization, that they lock things down in a way that makes sense, and that they not apply one-size-fits-all thinking."
#2: Bring in key stakeholders
Because data classification functions as the foundation for policies around security and compliance, you should work with the business and compliance areas of your organization to clearly define categories that make sense.
"The problem," says Anderson, "is often that the IT admin is the last person who should be doing it."
They should be working with those stakeholders. They should be the implementer and the sort of gatekeeper, but they should not make decisions without involving people who understand what they're trying to accomplish—it has to come from the people who understand the regulatory and statutory requirements.
Marc D Anderson, Microsoft MVP
He suggests using something called the RACI model:
- Responsible: The person responsible for doing the necessary work to achieve a task.
- Accountable: The person who's accountable for making sure the task is thoroughly and correctly completed.
- Consulted: People who provide input and information for the project via two-way communication, often subject-matter experts.
- Informed: Everyone who is kept informed of the project's progress via one-way communication.
"The IT quagmire is often that the IT admin takes on all of those roles even though they should maybe only have the 'Responsible' one."
With the RACI method, multiple key stakeholders are involved throughout the decision-making process. Senior arbiters in the "Accountable role"—which could be the CIO, or even the CEO depending on the size of the company—are the ones who sign off on and "own" decisions made over the course of the project. Someone from the legal department might lend their expertise as a consultant. And anyone else who will be affected, like end users, can just be kept up to date as needed via one-way communication.
#3: Create classifications that are clear and easy-to-understand
The beauty of Microsoft's classification scheme is how clear the classifications are. There are only four to choose from, and there's no ambiguity between one term and the next.
"It has to be simple and understandable," says Anderson.
I had a client who wanted something like 200 categorizations of content. They actually wanted to treat 200 things differently from a retention perspective, but nobody could look at it and understand it—not even the person who was responsible for it—because it was just too complex.
Marc D Anderson, Microsoft MVP
It's absolutely critical that your end users understand your classification scheme. Instead of 200 categories, Anderson suggests staying within the three- to the five-level range for your classification scheme.
The categories you choose should also help users understand the why of your classification scheme: what does it mean to apply one categorization over another? After all, users are the ones actually sitting in front of the keyboard trying to make the call on whether something is "confidential" or "highly confidential"—they need to understand what the difference is.
"It can't be complicated; it has to be words that people understand. They need to be able to follow through on the intent with as little friction as possible or else they won't do it."
Apply classification at the container-level (where it makes sense)
Once you have your classification scheme in place, there are many things you can implement building on top of it—such as sensitivity labels, Data Loss Prevention (DLP), and retention labels, just to name a few.
To make your life easier when it comes to customizing settings and policies, it's useful to apply classification at the container-level—i.e. at the Microsoft 365 group, team, or SharePoint site level—whenever possible.
"If you have a group of people that's working on something highly classified in a team within Microsoft Teams, you're probably going to apply the classification to that team," says Anderson. "It's just like the general idea of permissions; you apply it to the highest container level that makes sense so that people don't have to think about it."
When applying classification labels to containers, just make sure you err on the side of caution. As we mentioned before, applying a classification label actually does something. If you don't want to apply a "highly confidential" label to an entire team, applying it to a specific channel or simply creating a private channel or group might be better options.
"There's security and obscurity," says Anderson. "If you have a private group, people don't know what's there anyway, which sort of makes it obscure. The data classification stuff is more about security—you know, as an implied obscurity."



.svg)
%20(1).avif)