Secure sensitive data across Microsoft 365 with this smarter Teams security plan

Table of contents
With Microsoft Teams and modern SharePoint team sites being created at a record pace, how can you keep all of that content secured, protected, and retained? Microsoft MVP Joanne Klein (@JoanneCKlein) explains Microsoft Teams security and compliance.
Check it out: The ultimate guide to Office 365 / Microsoft 365 external sharing
In the early days of distributed work, many organizations fast-tracked security measures to enable remote collaboration. Today, with hybrid and remote work now fully embedded in how we operate—and AI accelerating content creation across Microsoft 365—the risks of accidental sharing, data leakage, and overexposure have only grown.
To keep Microsoft Teams content secure across the Microsoft 365 ecosystem, IT teams must implement security strategies that balance collaboration with control.
In her ShareGate webinar, Microsoft MVP Joanne Klein explained how Microsoft 365 features working together can help you breathe a little easier about Microsoft Teams security and compliance. In this recap article, we summarize some of her key points about keeping your Microsoft Teams content protected and secure.
Watch the webinar recording, or read through our recap of Joanne’s key points.
Jump to…
- Common challenges in managing data
- Data governance framework: Defining what is classified as sensitive data
- Container and content governance
- Security governance
- Discovery governance
- Key takeaways
Common challenges in managing data
With most business operations now cloud-based, a lot of sensitive data lives there too. But it’s hard to protect something if you don’t know where it is. And a vast amount of data, estimated to be about 90%, is unstructured and fragmented—making it harder for IT to locate and protect.
Nearly a quarter of all files in the cloud contain sensitive data that requires protection in order to reduce security risks.
The root of the problem in Microsoft 365 comes down to:
- Sprawl: It’s easy for users unfamiliar with Microsoft 365 to provision resources accidentally—resulting in confusion, lack of governance, and guests having access to things they shouldn’t.
- Shadow IT: If IT-approved systems aren’t meeting their needs, users aren’t afraid to turn to something that will—tools without IT oversight that make your organization especially vulnerable to sensitive data leaks.
The stats above demonstrate how widespread this concern is—these are real problems, and they can’t be dealt with using manual means.
So how do you keep up with all of this? Two key points:
- We need to leverage AI and automation to address this project at scale.
- We need to approach this as “proactive compliance”—have an information protection and governance strategy for security.
Both of these points require integrated solutions to come together in a cohesive way. Luckily, a lot of Microsoft 365 tools are already approaching security in a proactive rather than reactive manner.
A shared responsibility model
The fact of the matter is: not all teams are created equal (and not all data within them is the same).
Teams-work governance shouldn’t be one broad brush-stroke across all of your teams. At times, effective Teams governance requires a targeted application.
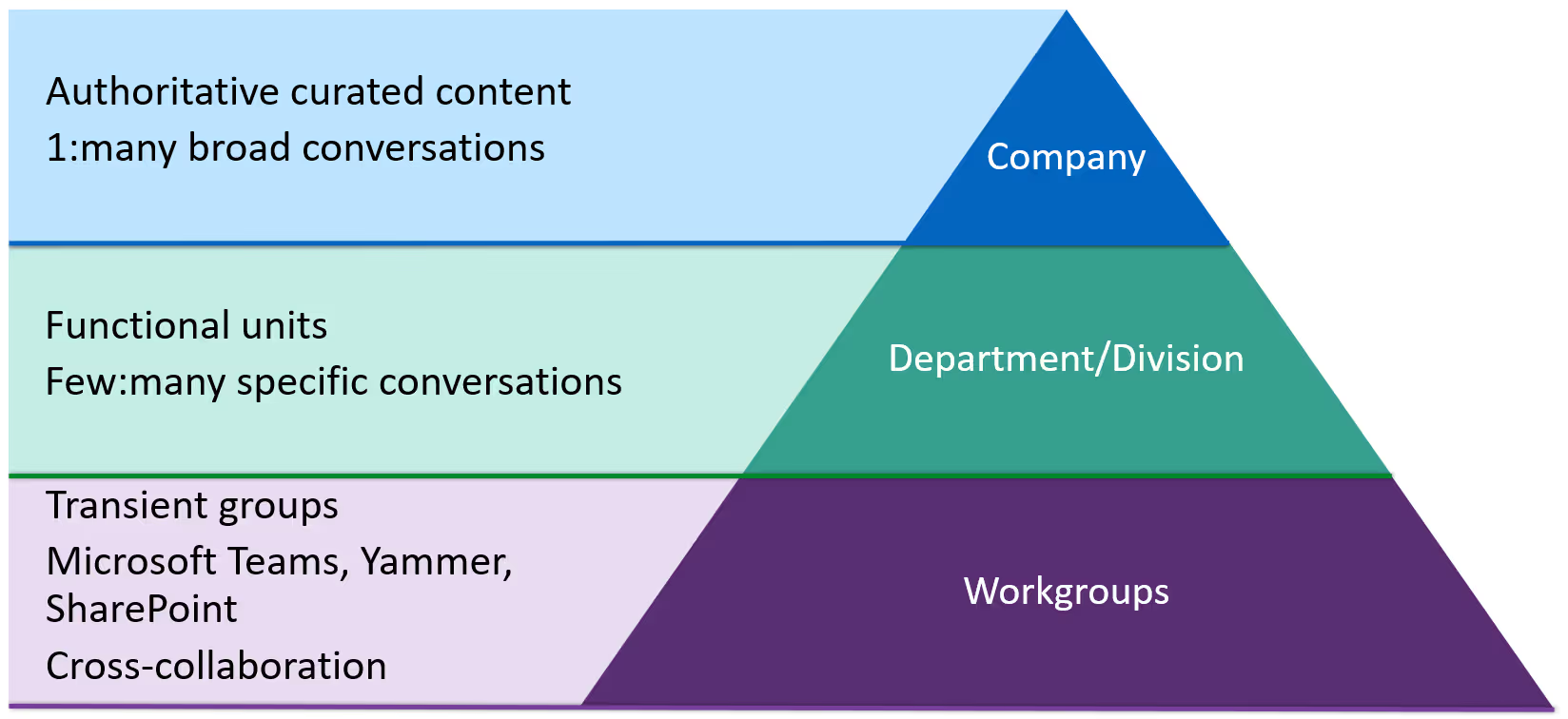
Within an organization, there are several roles—each with different perspectives and needs when it comes to Teams work and all of that unstructured content.
- The business: Accomplish business goals as simply as possible—if it’s too hard, find an easier way. Allow collaboration but still implement governance controls.
- Employees: Get work done efficiently with a minimal amount of friction. Keep things simple or they’ll find another way.
- IT admins: Manage the increasing volume of data, keep up with changing services and threats, and make sure all other roles are happy and productive.
- Legal: Ensure compliance with retention and eDiscovery.
- Risk & security officers: Prevent data leaks and breaches and protect high-value information.
One way to address these competing demands and requirements is to leverage a shared responsibility model—a cloud security framework that defines security obligations to ensure accountability.
Teams-work governance shouldn’t be one broad brush-stroke across all of your teams. At times, effective Teams governance requires targeted application.
Microsoft’s shared responsibility models says that you as an organization are responsible for protecting your data and identifying all devices with access. And Microsoft is responsible for protecting the Office 365 services. Together, you can protect your sensitive data from security threats.
Luckily, in today’s digital landscape, the Microsoft 365 Security and Compliance Center stands as a reliable ally for IT admins, empowering them with robust security management and regulatory compliance capabilities.
To get your electronic house in order, so to speak, a coordinated effort is required and involves three key groups:
- Business information workers: These are the people creating the content, sharing with external parties, and some of them are working with sensitive information. This group really needs to know how to work safely and securely in the modern workplace today—if they don’t then IT needs to teach them.
- IT teams: They control the resources that implement the technical controls involved as well as some of the training and configuration.
- Legal, risk, compliance, governance teams: These are the regulatory teams you need to help you define a classification system across your tenant. They’re in a unique position to understand what you need to do to protect data and remain compliant—lean into them, and bring them in from the start.
Data governance framework: Defining what is classified as sensitive data
The best way to approach data security and compliance is from the perspective of governance.
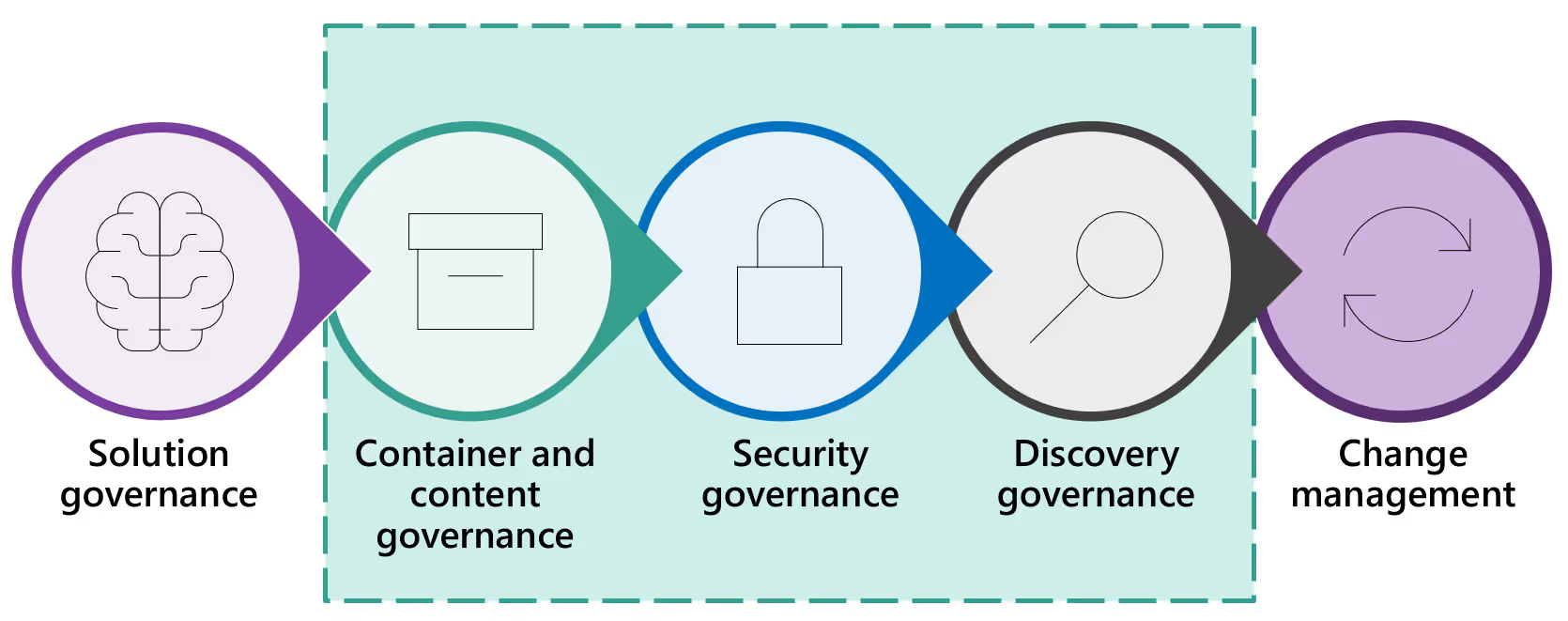
There are many different kinds of governance, all of which work together to ensure a governed and compliant environment end-to-end. But for now, we’re going to focus on three specific types:
- Container and content governance
- Security governance
- Discovery governance
1. Container and content governance
According to Joanne Klein, one of the best ways to tackle governance in your Microsoft 365 environment at scale is container governance: i.e., governance and security policies applied at the level of a container—in this case, at the level of a Microsoft team or Microsoft 365 group.
When we talk about container and content governance, we’re talking about what controls you can manage in Microsoft 365 and what level they’re applied to.
Container and content governance best practices can be broken down into the following tactics:
- Empower employees: Enable self-service site creation and lifecycle management so they don’t turn to shadow IT.
- Identify valuable content: Require classification for containers and scan with Data Loss Prevention (DLP).
- Protect valuable assets: Apply security and governance policies automatically according to data classification.
- Ensure accountability: Manage group/site ownership and review external membership.
Within the scope of this blog post, we’re going to focus on the middle two points: protecting and retaining your potentially sensitive Teams work—things that people in those legal and compliance areas will definitely be focused on.
Data classification: Identify your valuable content
Follow these steps to protect your sensitive Teams work wherever it lives:
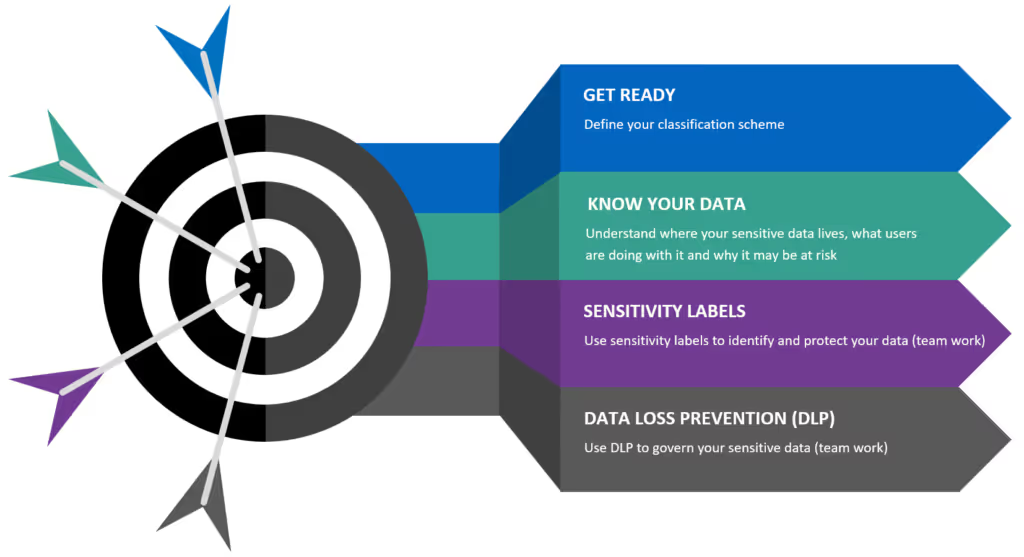
- Get ready: Define your classification scheme.
- Know your data: Understand where your sensitive data lives, what users are doing with it, and why it may be a risk.
- Label your data: Label your data according to level of sensitivity.
- Secure your data: Use automated governance policies to secure your sensitive data.
Thankfully, implementing Microsoft 365 security best practices can help you mitigate risks and secure your organization’s sensitive data by fortifying your defences and strengthening access controls.
Define your data classification scheme
Requiring classifications for your containers is the underpinning for absolutely everything else.
This is where you should work with the business and compliance areas of your organization to clearly define a classification scheme.
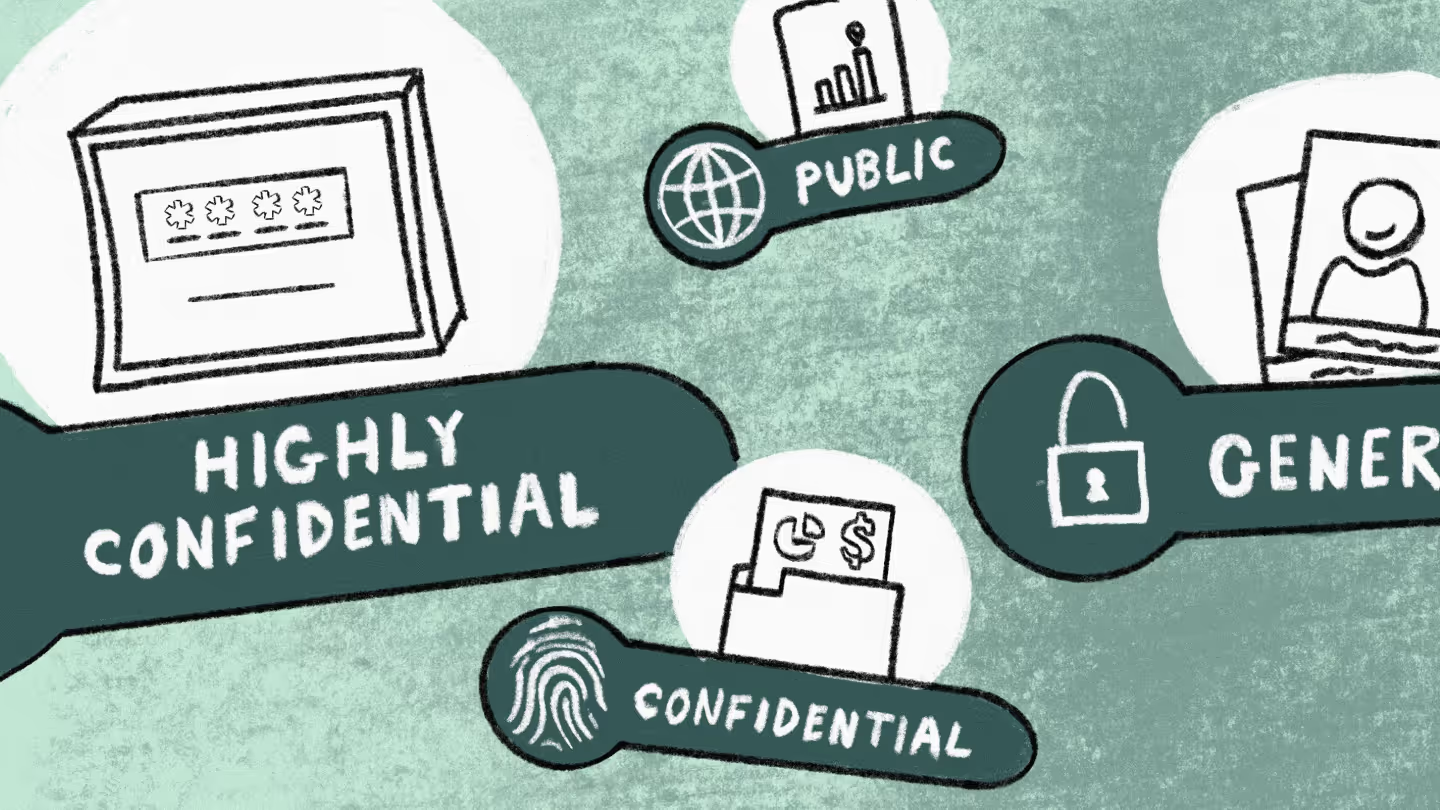
Microsoft’s classification scheme is impressive because they’ve managed to pare it down to just four categories:
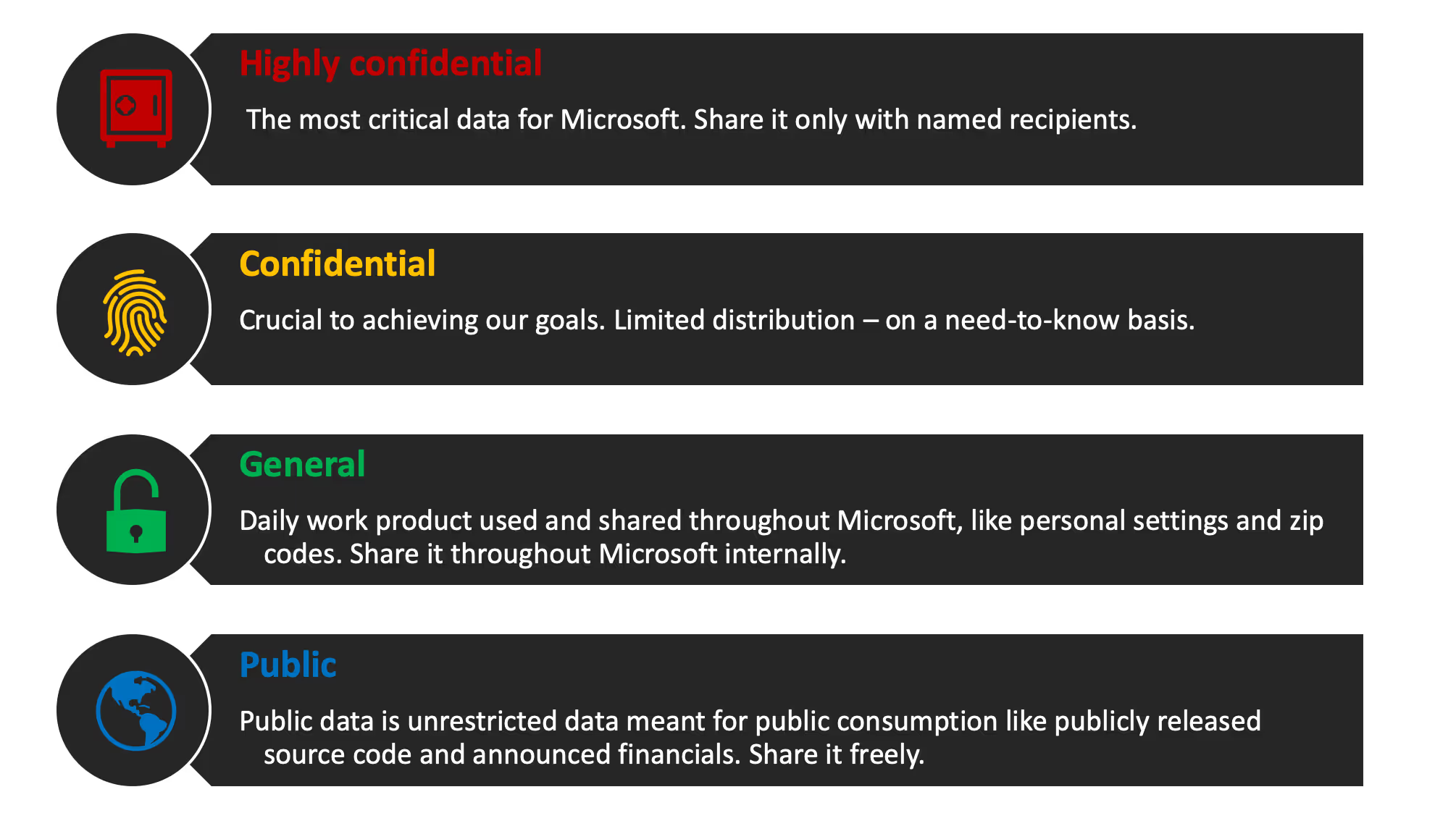
You don’t have to make yours the same as Microsoft’s, but there are some good takeaways to consider: namely, how clear and easy to understand the classifications are. There’s no ambiguity between one term and the next.
Ready to learn more? Check out our automated tool for Microsoft Teams Security, ShareGate.
It’s absolutely critical that your end users understand your classification scheme. They’re the ones actually sitting in front of the keyboard having to make the call on whether something is “confidential” or “highly confidential”—they really need to understand what the difference is.
So make sure your classification scheme is in terms that everyone can understand.
Use Microsoft Purview Information Protection (MIP) sensitivity labels to classify data
Once you have your classification scheme, there are many things you
can implement building on top of it. And one of the most effective is sensitivity labels.
Sensitivity labels let you classify and help you protect your sensitive content wherever it goes—without hindering your users’ productivity and ability to collaborate.
Tweet this
Built-in sensitivity labels from the Microsoft Information Protection (MIP) framework are managed through a single portal—the Microsoft 365 Purview portal—which unifies labeling and protection policy management across Microsoft 365 and Windows.
Sensitivity labels from the MIP solution let you classify and help you protect your sensitive content wherever it goes—without hindering your users’ productivity and ability to collaborate.
The end-user experience with sensitivity labels is available in:
- Office apps
- Office online
- iOS & Android (mobile)
- Sites and teams
- Teams meetings
- Microsoft Fabric (includes Power BI)
The user will see the same sensitivity label across all three platforms. This is derived from the data classification of your organization—a perfect example of why they need to be very clearly understood.
For further details, check out the official Microsoft documentation for common scenarios for sensitivity labels.
Secure sensitive data: Protect your valuable assets
In addition to classifying your data, sensitivity labels in Microsoft 365 can also be used to:
- Enforce protection settings like encryption or watermarks on labelled content
- Protect Microsoft 365 content across platforms and devices
- Extend sensitivity labels to protect content in third-party apps and services
- Protect containers that include Teams, Microsoft 365 groups, and SharePoint sites (requires an Entra ID Premium P1 license)
Sensitivity labels can be applied down to different levels. And you can now also apply it at a higher container label—at the level of an entire Microsoft team or SharePoint site. The beauty of that is that everything in that container inherits the same sensitivity setting by default.
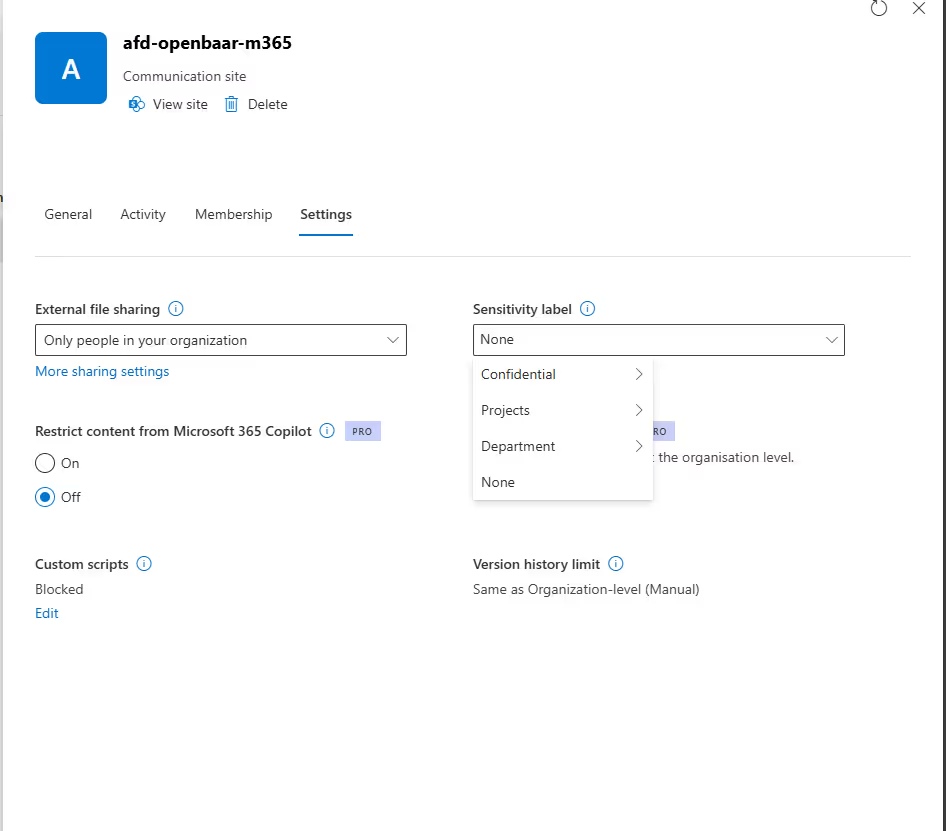
“Groups & sites” settings for sensitivity labels
Up until recently, it was only possible to apply sensitivity labels to emails or documents. Then, at Microsoft Ignite 2019, Microsoft announced the ability to apply even more controls with Groups & sites settings.
Now, in addition to using sensitivity labels to classify and protect documents and emails, you can also use sensitivity labeling to protect content in the following containers:
- Teams in Microsoft Teams
- Microsoft 365 groups
- SharePoint Communication sites
First announced at Microsoft Ignite 2019 and currently generally available, you can now apply even more controls with Groups & sites settings.
These settings are unified across Microsoft 365 groups, teams, or sites and let you configure:
- Privacy of Microsoft 365 groups and team sites: Determine the privacy settings (i.e. public or private) for that sensitivity label.
- External user access: Will you allow external users by default? You can choose to disable external user access for anything labelled as “confidential”—in which case Microsoft 365 group owners won’t be allowed to add external users.
- Access from unmanaged devices: If you have a confidential site, will you allow unmanaged devices to have access? You can choose to limit it so users on unmanaged devices have to use online versions of the Office products instead.
- External sharing from SharePoint sites: You can choose to limit external sharing to only people in your organization, existing guests, new and existing guests, or make sharing available for anyone.
Check out our recent blog article for more details on using sensitivity labels to protect sensitive content in Microsoft Teams sites, Microsoft 365 groups, and SharePoint sites.
To help you assess whether sensitivity labels in Microsoft 365 are the right fit for your organization, we decided to share what we learned in researching the capabilities and limitations of that feature and highlight some key differences between MIP sensitivity labels and ShareGate’s “Group sensitivity” feature.
“Files & emails” settings for sensitivity labels
Protection settings that can be applied to a document or email, including encryption and content marking, are configured by selecting the Files & emails scope. These capabilities have been around for longer and are what most people think of when they hear the term “sensitivity label”.
There are also two relatively new (extremely useful) sensitivity label features:
- Encrypted (protected) files. Encrypted files are now treated like first class citizens. You can open and edit directly in Office offline, co-authoring is allowed, and they are searchable (allowing for DLP and eDiscovery)—improving that collaboration experience for end users.
- Auto-labeling files at rest in SharePoint. If you have some docs that aren’t labeled, there is an auto-labeling feature that ensures they’re labeled automatically. This is extremely useful for if users forget to set a label. (Additional licensing requirements. You can read more about the licensing requirements for Microsoft Information Protection here.)
Check out our recent guide for more details on how to use Microsoft Information Protection (MIP) sensitivity labels and how to configure settings at each label scope.
Data Loss Prevention (DLP)
This is another way of preventing accidental or unwanted exposure of your sensitive info.
DLP uses a content analysis engine to scan the contents of email messages and files looking for sensitive information. If detected, DLP lets you:
- Actively block the email or file sharing
- Display a warning to the user who is sending or sharing the sensitive information
- Log the event for auditing purposes
DLP is built on sensitive information types, which you can base off retention labels or Microsoft PurviewInformation Protection labels (but soon you’ll be able to do it through UI as well).
DLP policies can be set and configured in the Microsoft Purview admin center by selecting Data loss prevention underneath Solutions in the left-hand navigation. From the Policies tab, click on Create a policy to set a new DLP policy.
You can choose to use one of the DLP policy templates provided by Microsoft 365, or customize your own.
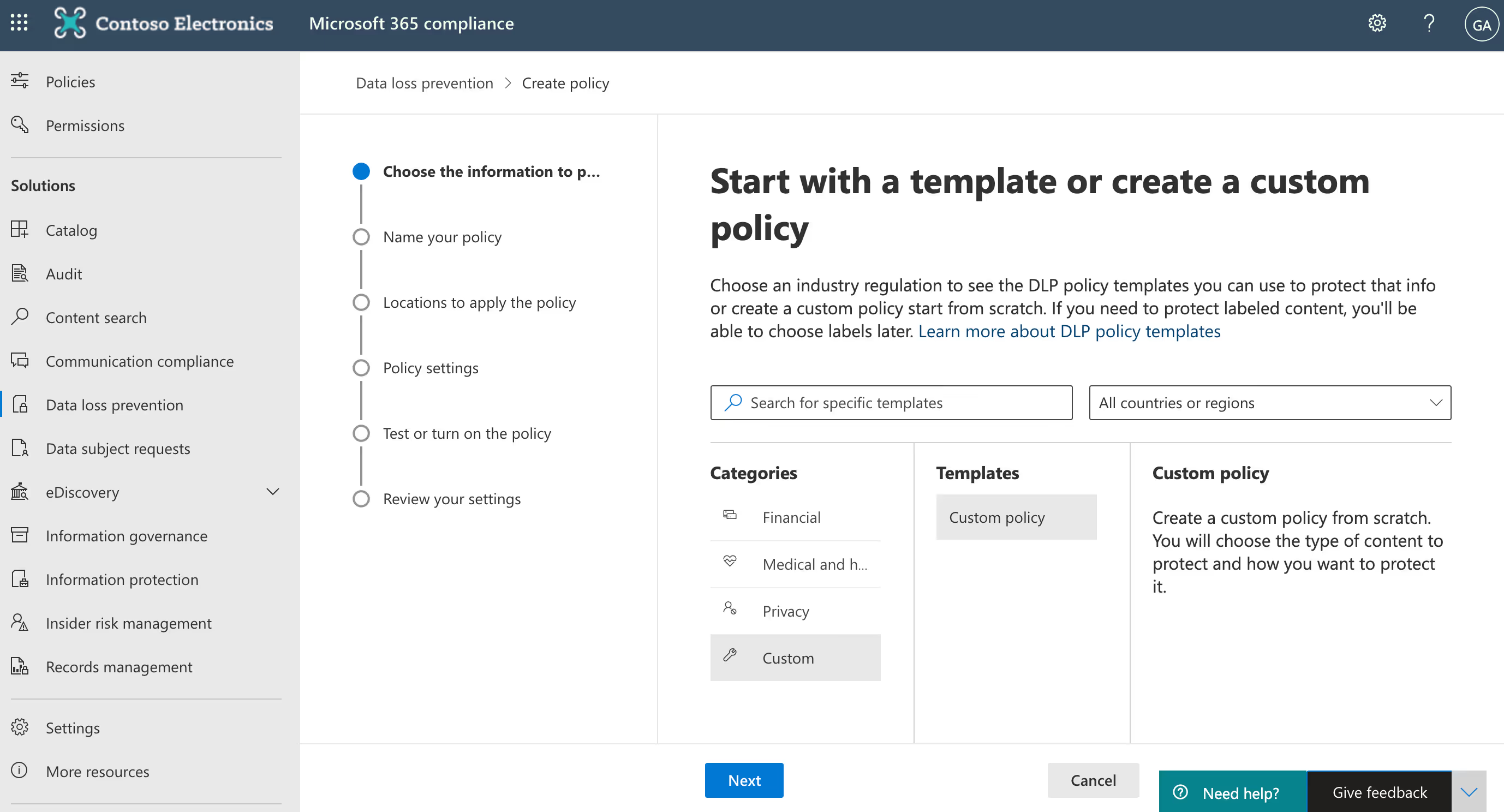
You can also choose where to apply your policy—across Exchange email, OneDrive and SharePoint documents, and/or Teams chat and channel messages.
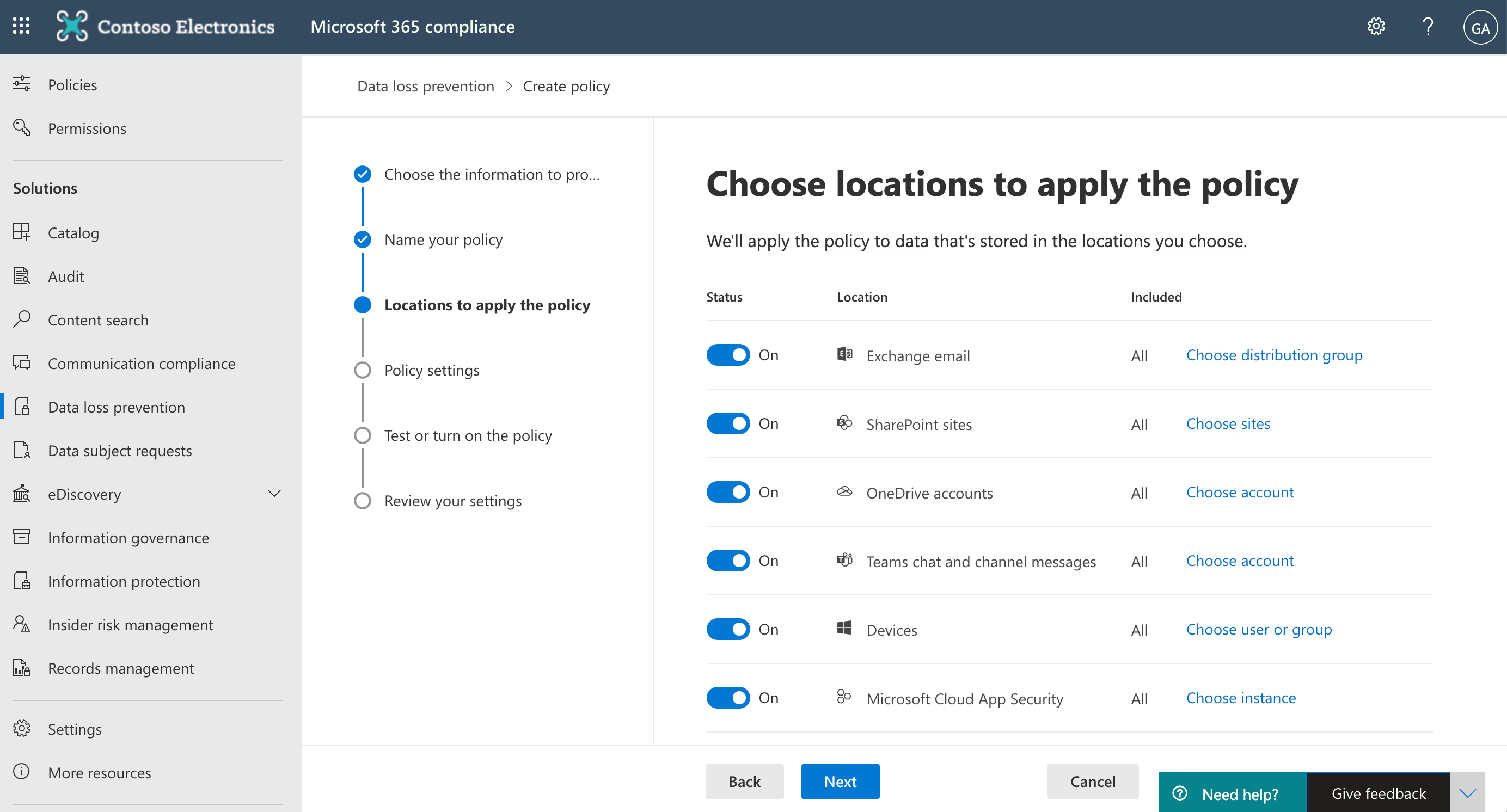
DLP is now integrated with Teams to block sensitive content when it’s being shared. This includes users with guest access and external access, and works on both the Teams desktop app and web app.
You can even test out your DLP policies ahead of time, before you turn them on live across your environment. That way, you can start to get a feel for the accuracy of your policy and how effective it will be when it’s enforced—and fine tune it if you need to.
Some other key features to take note of:
- Block anonymous access for sensitive files in SharePoint Online and OneDrive for Business.
- Enforce DLP controls based on sensitivity labels.
- Treat brand new files in SharePoint Online as sensitive by default until scanned by DLP (which works on a scanning mechanism and isn’t immediate).
Note: Data loss prevention capabilities were recently added to Microsoft Teams chat and channel messages for users licensed for Office 365 Advanced Compliance, which is available as a standalone option and is included in Office 365 E5 and Microsoft 365 E5 Compliance. To learn more about licensing requirements, see Microsoft 365 tenant-level services licensing guidance.
Retention policies and retention labels
The information and records management teams in your organization will probably be most concerned with retaining the records of your Microsoft Teams.
The idea behind retention in Microsoft 365 is built-in compliance. It’s retaining in place—not moving something outside of Microsoft 365 to an external archive. The advantage to that is that it’s still discoverable, and there’s also an audit trail.
You have three options when it comes to applying retention across your Teams work:
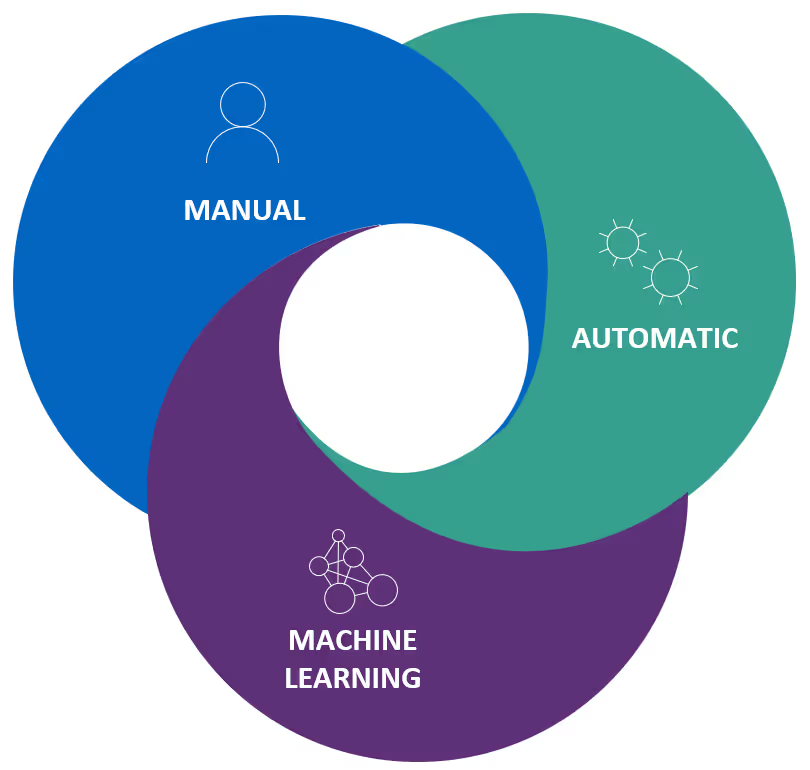
- Manually applied: The end user applies a retention label on a specific document or email.
- Automatically applied: Retention can be automatically applied based on location, sensitive information type, keyword, content type, or metadata.
- Machine-learning applied: Using machine learning to apply a retention label based on a trainable classifier.
Remember what we said before about using AI and automation to tackle data security at scale? Soon you’ll be able to auto-apply a retention label based on a trainable classifier.
Now available, trainable classifiers are powered by machine-learning and come with six built-in classifiers, plus the ability to build your own custom classifiers.
The retention capabilities available to you will depend on the licensing possessed by your organization. Head to the Microsoft 365 licensing guidance for security & compliance documentation for more details.
Understand and keep tabs on your data classification
In order to protect your sensitive data, you need to understand where it lives, what users are doing with it, and why it may be at risk.
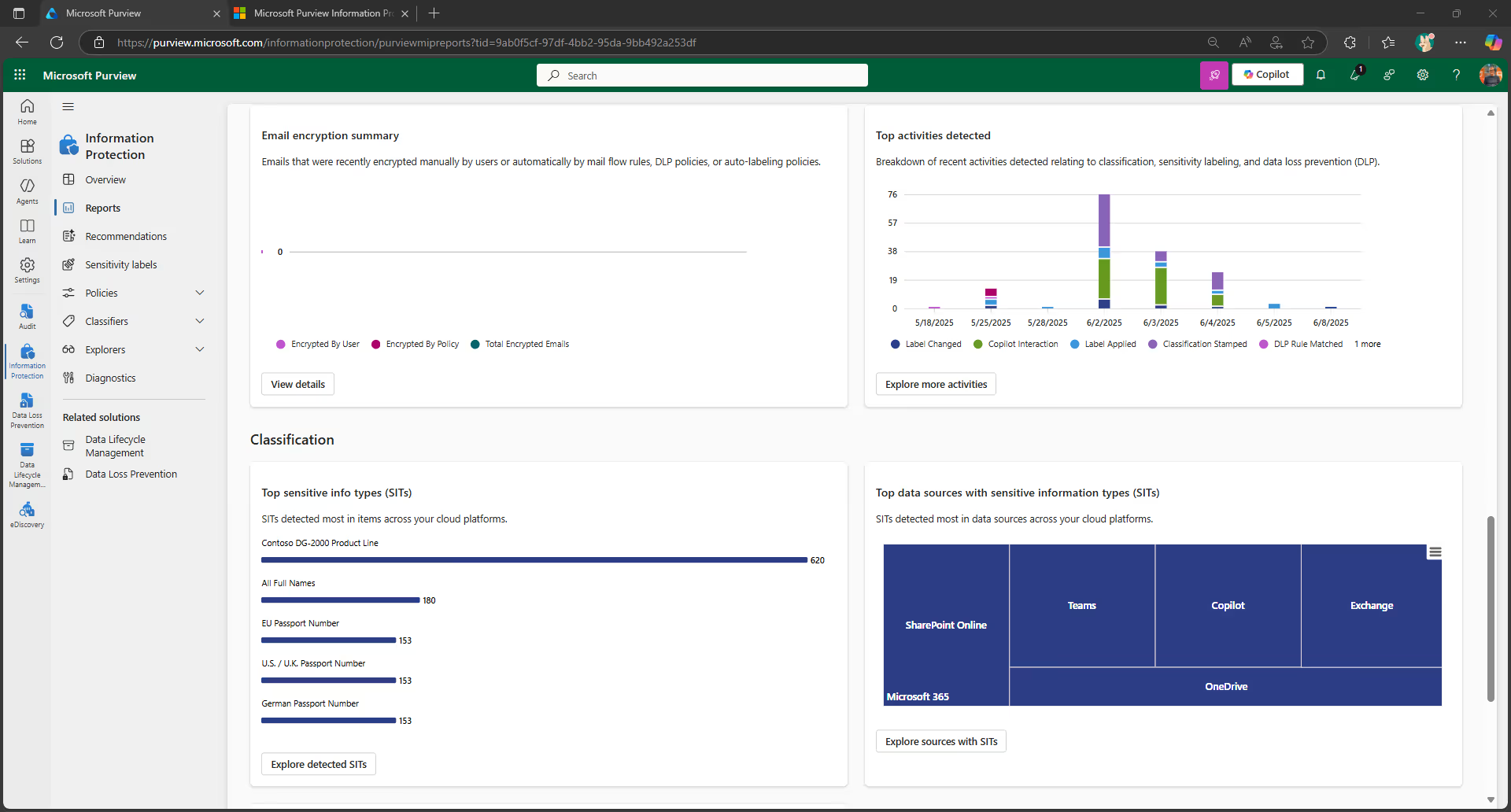
Once you’ve created your retention and sensitivity labels, you can track how they’re being used across your tenant on the Data classification page in your Microsoft Purview admin center.
For example, you can see:
- The number of items that have been classified as a sensitive information type and what those classifications are
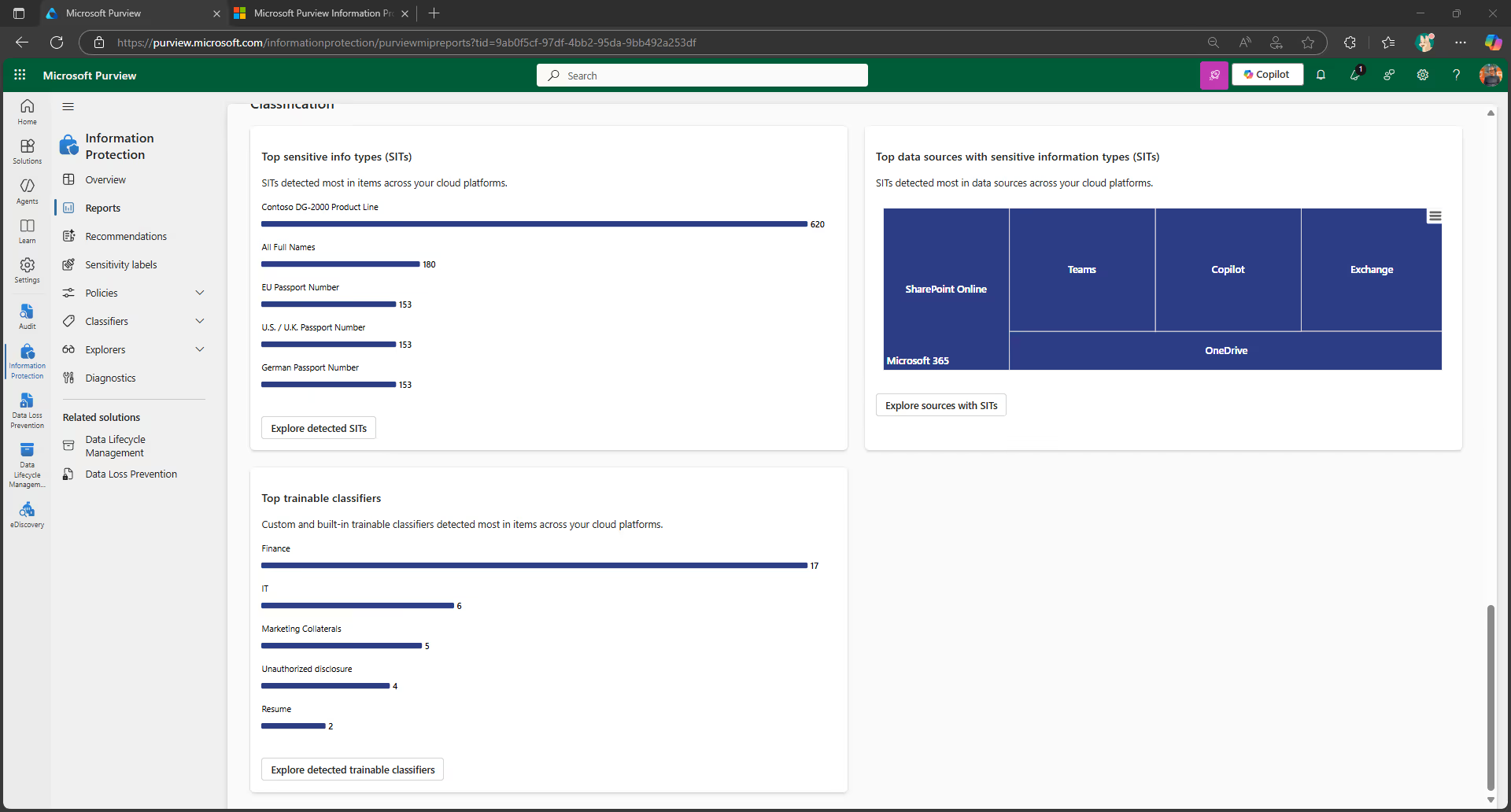
- The top applied sensitivity labels in Microsoft 365
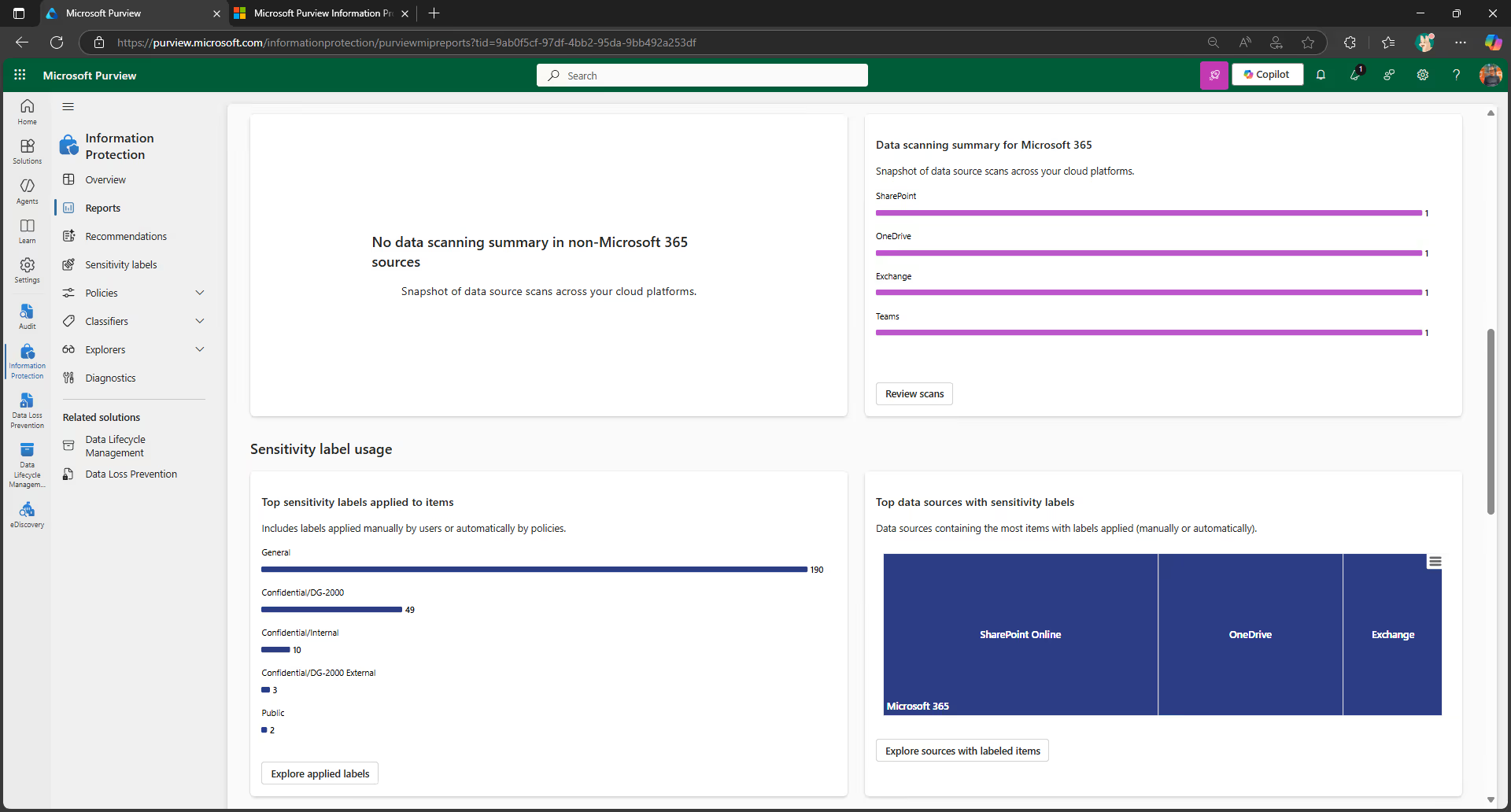
- The top applied retention labels
- A summary of activities that users are taking on your sensitive content
- The locations of your sensitive and retained data
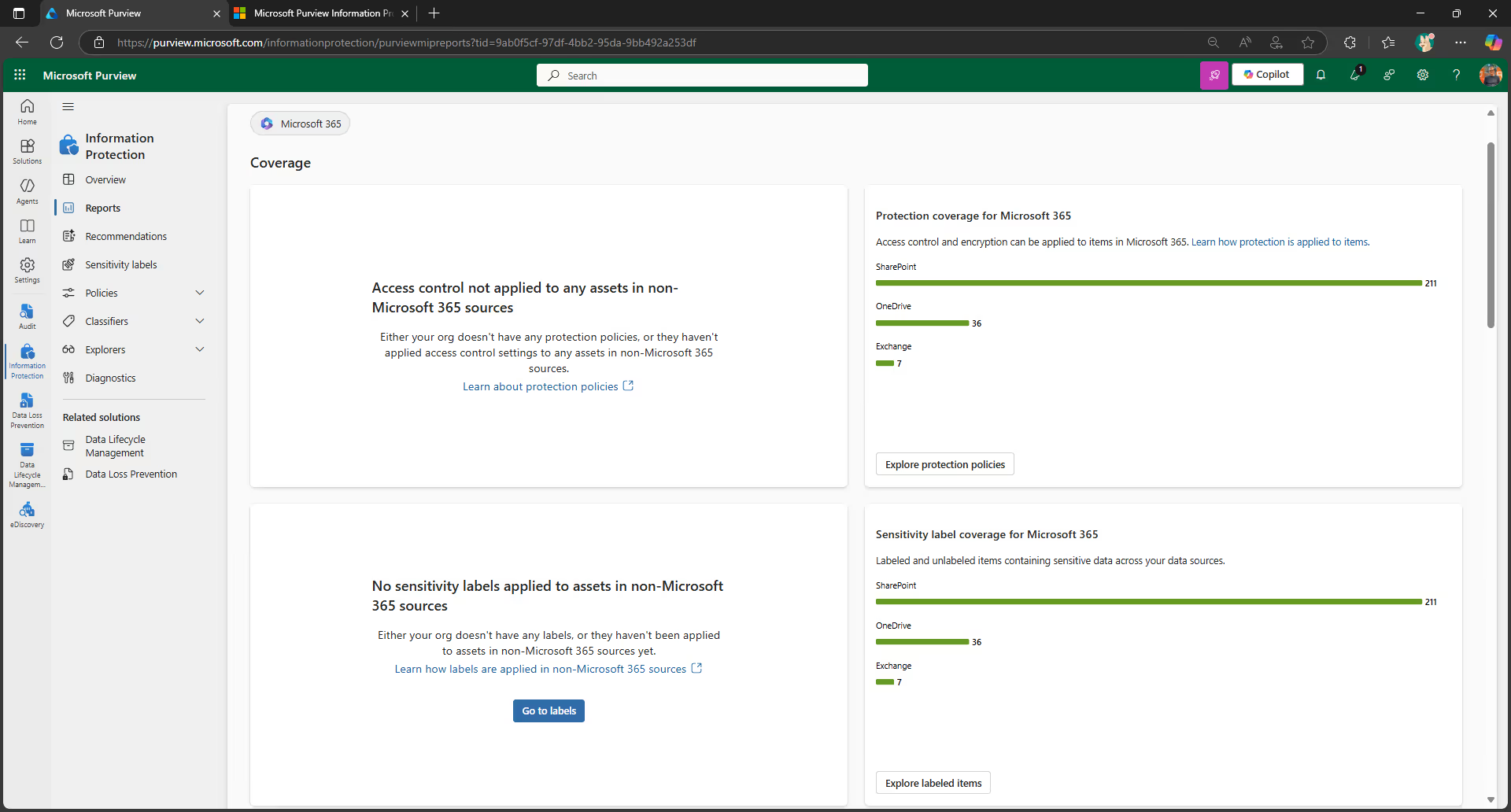
Understanding how labels are being utilized across your organization can help you better refine your protection and governance policies over time.
For more details on label analytics, check out the official Microsoft documentation.
2. Security governance
You definitely want to have external sharing enabled. But how can you ensure that external collaboration remains secure? That’s where security governance comes in.
External access vs guest access in Microsoft Teams
When collaborating with users external to your organization, it’s important to understand that external access and guest access mean two very different things in Teams.
External access gives access permission to an entire domain—allowing Teams users from other domains to find, contact, and set up meetings with you. External users can call you through Teams and send instant messages. But if you want them to be able to access teams and channels, guest access might be the better option.
Guest access is when you invite an external user to be a member of the team—it gives access permission to an individual rather than a domain. Once a team owner has granted someone guest access, they can access that team’s resources, share files, and join a group chat with other team members.
If you’ve set up your DLP policy to protect your Teams chats and channel conversations, that applies to conversations with guest access users, too.
This is a huge benefit! If your organization is going to collaborate with external users anyway, you can invite them to become guest access users in Teams.
If you’ve set up your DLP policy to protect your Teams chats and channel conversations, that applies to conversations with guest access, too.
Tweet this
That way, the data is kept in your tenant where you can protect it, monitor it, and control it. That’s much better than if you don’t allow sharing and people simply go around you and your approved tools.
Collaborating with external users securely
To protect your sensitive information, you need to have a strategy for collaborating securely with external users.
These external sharing recommendations can help you get started on the right foot:
- Collaboration: Enable external sharing by default, disable based on classification.
- Domains: Limit domains as required.
- Educate: Educate your users on how to share and what to share.
- Anyone links: You can now use DLP to prevent the creation of “Anyone” links for sensitive SharePoint and OneDrive for Business documents.
- Audit: Make security audits part of your governance process.
For full details about external sharing and how to ensure it stays secure, check out our Ultimate guide to Office 365 external sharing.
3. Discovery governance
Discovery governance concerns the discoverability of your Teams work—specifically with regards to eDiscovery.
Electronic discovery, or eDiscovery, is the process of identifying and returning electronic information that can be used as evidence in legal cases. You can use eDiscovery in Microsoft 365 to search against all of your workloads and find content relevant to the case.
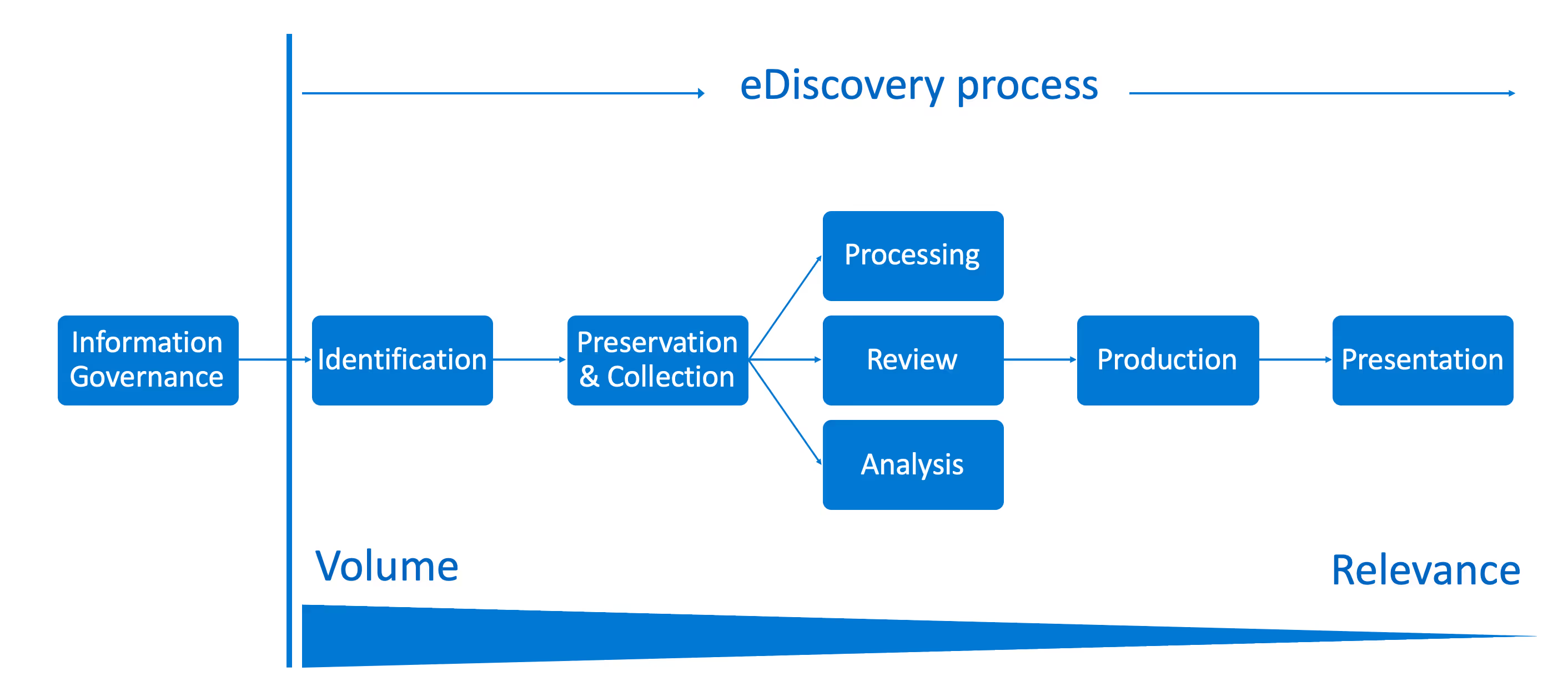
Looking at the eDiscovery reference model above, you can see how all the different controls we’ve talked about up until now are necessary precursors to your content’s discoverability.
Microsoft 365 currently provides the following eDiscovery tools:
- Content search in the Microsoft 365 compliance center
- Core eDiscovery in the Microsoft 365 compliance center
- Advanced eDiscovery solution in the Microsoft 365 compliance center
With eDiscovery tools, you can do things like redact sensitive content and use electronic holds (retention policies) to retain content.
As of very recently, you can reconstruct a Teams conversation with eDiscovery, too—allowing you to see the context of a conversation—and discover a user’s teams automatically. Both of these new features make life a lot easier for your legal team.
The eDiscovery capabilities available to you will depend on the licensing possessed by your organization. Head to the Microsoft 365 licensing guidance for security & compliance documentation for more details.
Key takeaways
If you’re just starting out, these four high-level points are a great place to start:

- Classifications: Document your organization’s data classifications.
- External user strategy: Establish your external user strategy for collaboration—including guest access, external access, and external sharing.
- Enforce policies: Determine policies to enforce based on the classification: sensitivity, retention, privacy, guest access, and conditional access.
- Educate users: Educate and train information workers across your organization on “e-safety in the org”.
We said it before and we’ll say it again: you need to leverage AI and automation to address this project at scale. A third-party governance tool like ShareGate can help you stay on top of security as you scale. Get full visibility into who’s shared what with whom, and automate external sharing reviews so they’re performed on an ongoing basis.


.svg)
%20(1).avif)