Microsoft 365 vs on-prem security: A decision framework
Table of contents
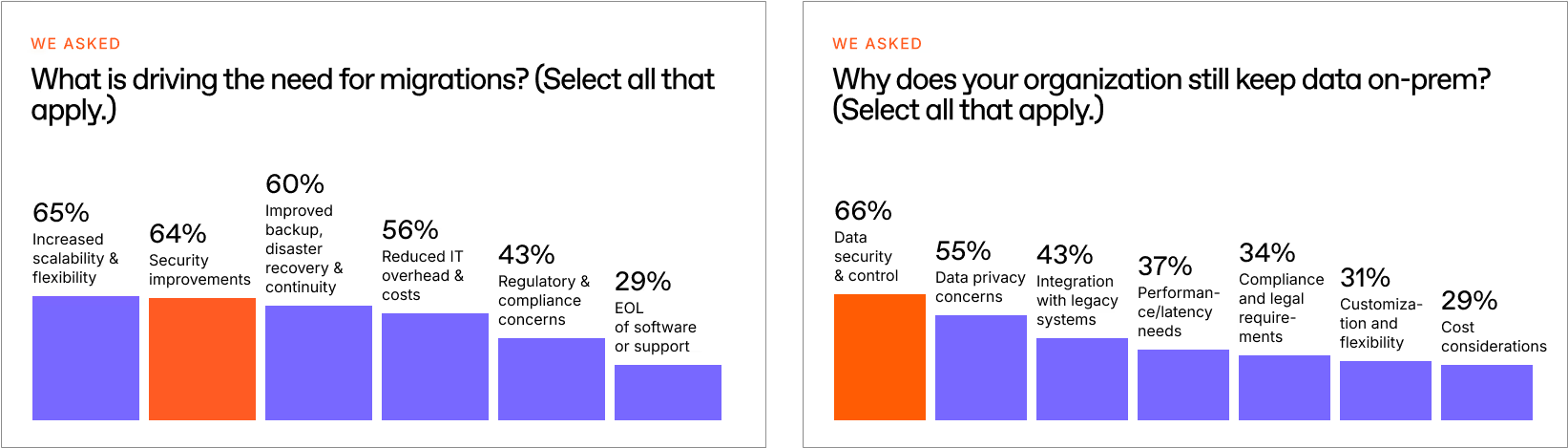
In our survey of 650 Microsoft-focused IT pros, 66% said they moved to the cloud for security, yet 65% keep some critical workloads on-prem for the very same reason.
With SharePoint Server 2016/2019 hitting end of support in July 2026 and Microsoft’s EU Data Boundary keeping most Microsoft 365 customer data in-region by default, the security conversation is shifting from blanket policies to workload-by-workload decisions.
We’ll explore why teams see security differently, then walk through a practical scorecard to decide what moves to the cloud—and how to minimize risk if a small carve-out must stay on-prem temporarily
What “security” actually means in Microsoft environments
Before we compare SharePoint Online vs on-prem security, it helps to look at security through two lenses:
- The control plane - Identity, access, monitoring—things you do to protect data
- The data plane - Where the data lives, the laws that apply to it, and who can lawfully access it).
And that’s why smart people can disagree without anyone being wrong.
“Security means different things to different teams. In the cloud, you get security services like conditional access and multi-factor authentication, but some feel like they’re more in control when they can touch the servers. I do get where those people are coming from, especially for people who are concerned about where their data is being stored.” - Microsoft MVP Jasper Oosterveld in The state of Microsoft 365 report
Most confusion comes from mixing these up.
READ MORE: Learn how your peers are approaching Microsoft 365 security in The State of Microsoft 365 report
Control-plane security—where cloud usually wins
In practical terms, Microsoft 365 security best practices are easier to implement and keep current in the cloud because the capabilities live in the platform and update continuously:
- Identity and access: Entra ID Conditional Access, MFA, risk-based sign-in, and Privileged Identity Management (PIM) help you enforce Zero Trust without custom builds.
- Threat protection and telemetry: Native Defender integrations and the unified audit log speed investigations and strengthen evidence for Microsoft 365 compliance.
- Governance at scale: Microsoft Purview (sensitivity labels, DLP, retention) plus clear provisioning rules turn permissions governance in Microsoft 365 into a continuous process—not an annual fire drill.
- Secure defaults: Baseline policies, continuous patching, and platform hardening reduce the “forgot to update that server” problem. You inherit a lot of good hygiene by default.
The takeaway: if your biggest risks are identity attacks, oversharing, or gaps in monitoring and auditability, Microsoft 365 gives you more control-plane leverage with less custom engineering.
Data-plane security—why some data feels “safer” on-prem
The data plane is about custody: where content resides, which jurisdiction applies, and who can require access. That’s where on-prem can still look attractive in specific scenarios:
- Residency & sovereignty: The EU Data Boundary helps many EU/EFTA customers keep Microsoft 365 data in-region by default, but some workloads still warrant a closer look with legal and compliance teams.
- Lawful access & contracts: Highly sensitive records subject to sector rules (e.g., public sector, defense, certain health contexts) may trigger additional approvals, key management needs, or contractual constraints before moving to the cloud.
- Latency & legacy ties: If a SharePoint farm powers an on-prem line-of-business app with tight latency or bespoke integrations, moving the data could break something mission-critical—at least until you modernize that dependency.
- Time-boxed carve-outs: SharePoint Server Subscription Edition (SPSE) can maintain custody for a subset of data while you resolve residency, contract, or integration blockers—with exit criteria and reviews so ‘temporary’ doesn’t become ‘forever.’
The takeaway: if your blockers are legal, contractual, or tied to immovable integrations, the debate isn’t “cloud vs on-prem” in general—it’s which specific workloads need a short-term exception and what would have to change to move them.
Common misconceptions to retire
A few myths get in the way. Let’s retire them:
- “On-prem is safer by default.” Security depends on controls you operate, not the building your servers sit in. Many breaches start with identity—not storage location.
- “Cloud is public, so it’s less secure.” With Conditional Access, MFA, continuous patching, Copilot, and Purview, the cloud often gives you more practical control—especially at scale.
- “Compliance is automatic in Microsoft 365.” Platform features help, but Microsoft 365 compliance still requires configuration, documentation, and ongoing reviews.
- “Hybrid is a security strategy.” Hybrid is an operating state, not an outcome. A hybrid cloud security strategy still needs defined controls, owner accountability, and a plan to retire exceptions once residency or integration hurdles clear.
Keep these distinctions in mind as you evaluate SharePoint Online vs on-prem security. In the next section, we’ll use them to score each workload—so you can decide what moves now, what (if anything) stays temporarily, and why.
With the terms straight, let’s ground this in timing and support realities.
Lifecycle and compliance: SharePoint 2016/2019 end of support
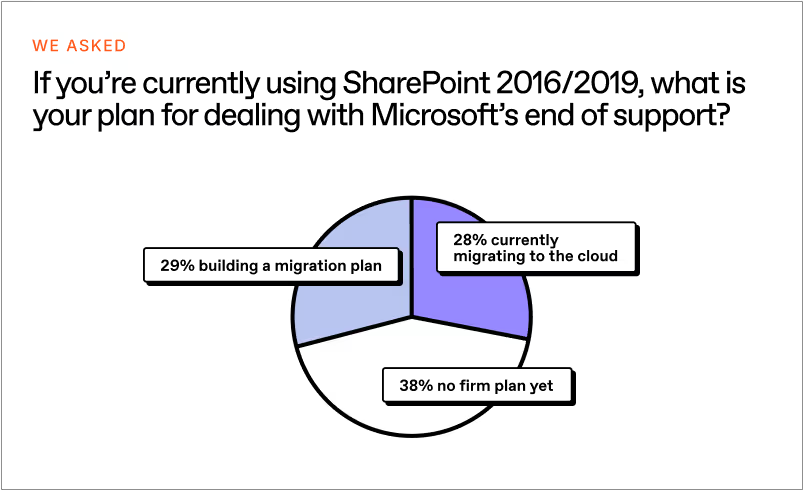
We all know the SharePoint on-prem EOS date is coming in fast, yet of the 650 IT pros we surveyed, 78% said they were still using SharePoint on-prem, and a third of those people still didn’t have a plan for July 2026.
If that sounds familiar, you’re not alone. Teams are juggling legacy integrations, residency sign-offs, and change freezes—totally valid reasons to pause. The catch is the calendar doesn’t slow down.
So let’s ground the discussion in the lifecycle reality—what’s supported when and where. Here’s a quick snapshot of support models and what they mean for risk:"
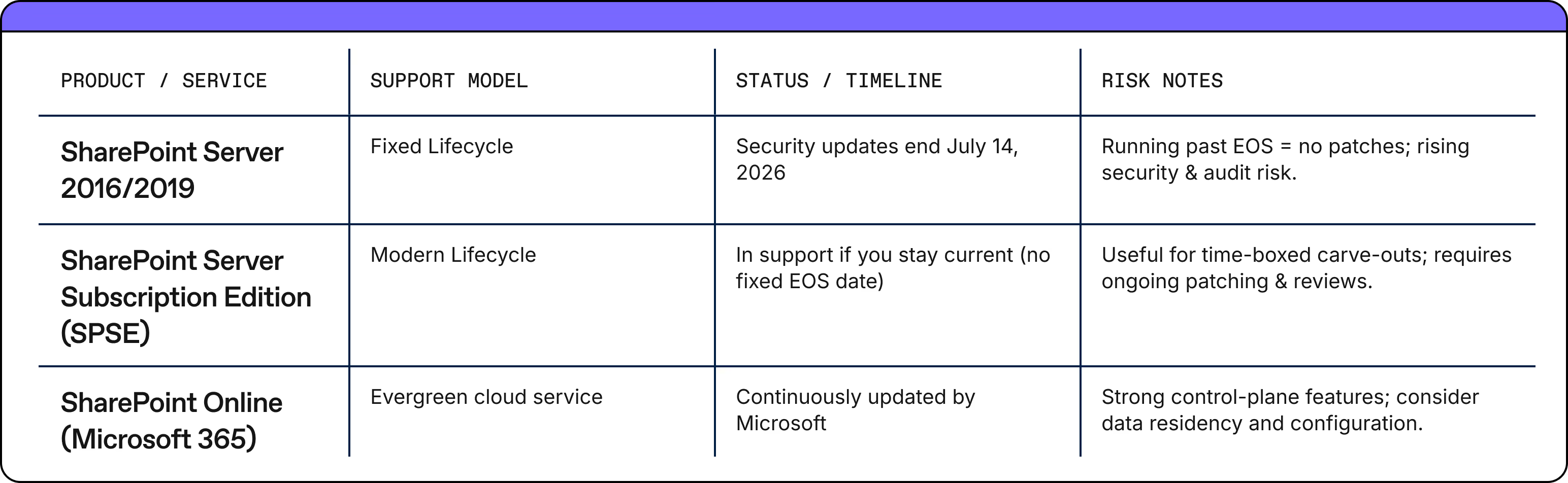
Patches age like milk, not wine, so plan accordingly.
READ MORE: Get all the details on SharePoint server EOS and advice on what your next steps should be in our eBook written by Microsoft MVP Richard Harbridge.
Cloud, hybrid, or SPSE: A Microsoft 365 security decision framework
Even though here at ShareGate we’re big fans of a cloud-first approach, we know there’s no one-size-fits-all answer. Real organizations have real constraints—regulatory quirks, data residency, legacy integrations, timing.
So instead of pretending there’s a universal prescription, we built a decision framework to help you choose the best path for each of your workloads.
Most teams already trust Microsoft 365 on compliance (60% very confident, 39% somewhat, only 1% not confident), but migrations still run on “trust-and-verify.” That’s why this framework bakes in auditability and residency—so you can show your work before anything moves.
Here’s the method: Start with a quick gates check to catch any hard blockers. If you’re clear, add a few points for signals that make cutover trickier, then subtract cloud advantages your stakeholders actually need (things Microsoft 365 does materially better). The total gives you a defensible path—cloud-first now, a short pilot with mitigations, or a time-boxed SPSE exception. It keeps choices consistent, auditable, and defensible.
Microsoft 365 security decision framework
Step 1: Hard blockers
If your organization has any of these, keep it on-prem for now and assign an owner and target date to unblock it.
- Contract or regulatory prohibition on cloud processing or storage is still in force.
- Residency isn’t finalized and Multi-Geo/ADR aren’t approved for the required regions.
- Full-trust farm solutions (WSPs), server-side code, or timer jobs are in active use with no re-platform plan to SPFx, Graph, or Power Platform.
- Bespoke integration depends on direct SQL, content DB access or unsupported APIs and components in SharePoint Online.
- Network and latency SLOs can’t yet be met over WAN to Microsoft 365 (e.g., CAD/PLM/video libraries, plant floor apps).
- Keys must remain entirely on-prem (e.g., HSM mandate) and Customer Key isn’t accepted as equivalent.
*Quick residency note: the EU Data Boundary plus Multi-Geo/ADR may satisfy many EU/EFTA cases—if so, treat “Residency not finalized” as a temporary gate and set the approval step as your burndown item. If you need even tighter control, Microsoft now offers Data Guardian and External Key Management to add sovereignty safeguards while staying in the public cloud, and Microsoft 365 Local for organizations that must run Microsoft 365 in their own datacenter. (Availability varies by region.)
Step 2: Strong indicators (+1 each)
These aren't full-on blockers, but they make immediate cutover harder. Add a point for each that applies.
- Legacy or bespoke integrations (LoB, event receivers, BDC, scanner imports, in-house add-ins) need refactoring.
- Data gravity and complexity (multi-TB libraries, extreme file counts, deeply nested permissions).
- RBS or cheap storage (Remote Share Provider/SMB offload) you’re not ready to replace.
- Hybrid Search required (align farm to SPSE 25H1+ going forward).
- Auth mid-transition (apps still rely on non-modern auth).
- RMS/IRM dependencies not yet redesigned for sensitivity label encryption.
- Tight change-control windows or seasonal freezes right now.
- IR/backups still centered on on-prem; not ready for Microsoft 365 Backup or SaaS backup.
- Classic customizations (classic publishing, JSLink, InfoPath) that need redesign.
- Local or isolated operations (regulated labs, defense, disconnected plants).
- Missing governance baseline (sharing defaults, lifecycle, provisioning, naming, labels).
- Role clarity and/or owner readiness (labels, retention, sharing, training) not in place.
- Incident and eDiscovery not transitioned to Microsoft Purview workflows.
Step 3: Cloud advantages you need (−1 each)
If stakeholders expect these in the next 12 months, subtract a point per item—they tilt you toward cloud.
- Information protection and governance: Purview sensitivity labels (with encryption or usage rights), retention (auto-apply or event-based records), unified DLP, site orcontainer labels and default doc labels.
- Threat protection: built-in antimalware at rest; Defender for Office 365 Safe Attachments for SharePoint Online, OneDrive, and Teams.
- Access control: unmanaged device controls (Conditional Access app-enforced restrictions), Defender for Cloud Apps session controls, SharePoint Advanced Management (e.g., Restricted Access Control), Information Barriers v2.
- Audit and discovery: Unified Audit or Audit (Premium) retention and events; Purview eDiscovery (Standard or Premium).
- Encryption and keys: per-file service-side encryption; Customer Key (BYOK).
- Resiliency and recovery: self-service Restore this library, deleted site recovery, Microsoft-assisted backups; Microsoft 365 Backup at scale.
- Data residency choices: Multi-Geo or ADR for at-rest placement across regions.
Step 4: Decide the path (add up your points)
If any gate in Step 1 is checked → keep on SPSE/hybrid for now and create a plan for addressing it.
Otherwise, total Step 2 points and subtract Step 3 credits.
- Total ≥ 6 → Stay SPSE/hybrid for now. Publish your burndown and re-score next quarter.
- Total 3–5 → Hybrid with aggressive blocker burndown. Pilot in Microsoft 365, close top gaps, re-score quarterly.
- Total ≤ 2 → Cloud-first migration to SharePoint Online. Plan your waves and go (with Conditional Access, MFA, and Microsoft Purview controls as table stakes).
Once you land on your path, get moving. If you need a nudge to avoid analysis paralysis, we love this reminder:
“Teams often agonize over theoretical gaps while ignoring the fact that their current state isn’t perfect—it’s probably less secure.” - Microsoft MVP Joanne Klein, in The state of Microsoft 365 report
Key takeaways and next steps
If there’s a theme here, it’s clarity over dogma.
Cloud-first makes sense for most Microsoft teams because you get stronger day-to-day controls—Conditional Access, MFA, auditing, labeling—without a ton of custom work. But real life has edges: residency rules, old line-of-business ties, merger timelines.
That’s why the scorecard exists. It helps you make the call workload by workload, document why, and keep exceptions from turning into forever.
Remember, security isn’t a place—it’s the set of controls and practices you can sustain.
If you need help securing your Microsoft 365 environment, book a call with one of our experts to see how ShareGate can help.


.svg)
.avif)
%20(1).avif)







.avif)