Microsoft Teams security: Comparing Microsoft Information Protection unified labeling and ShareGate's sensitivity tags

Table of contents
Wondering how to stay on top of Microsoft Teams security? To answer that, we compare sensitivity labels in the Microsoft Purview admin center with ShareGate's sensitivity tags.
Check it out: The ultimate guide to Microsoft 365 sharing
Keeping organizational data secure is a top priority for IT admins today. And, according to Microsoft MVP Joanne Klein, one of the best ways to approach data security at scale is from the perspective of container governance: security and compliance policies applied at the level of Microsoft teams and Microsoft 365 groups.
Our engineers did a ton of research into container-level data protection while developing our ShareGate release. And a large part of that process included looking at unified sensitivity labeling in the Microsoft Purview admin center to understand the capabilities and limitations of that feature. Explore our Microsoft Teams security solutions here.
To help you assess whether Microsoft Information Protection (MIP) sensitivity labels are the right fit for your organization, we decided to share what we learned and highlight some key differences between MIP sensitivity labels and ShareGate's sensitivity tag feature.
Sensitivity labels in the Microsoft Purview admin center
Sensitivity labels in Microsoft 365 have been around for a while, with their evolution tracing back to Information Rights Management within Microsoft 365, then Azure Information Protection (AIP) in the Azure portal, and finally, unified labeling through the Microsoft Purview admin center.
Built-in sensitivity labels from the Microsoft Information Protection (MIP) framework are managed through a single portal—the Microsoft Purview admin —which unifies labeling and protection policy management across Microsoft 365, Windows, and file shares.
Sensitivity labels from the MIP solution let you classify and protect your organization's data while making sure that user productivity and their ability to collaborate aren't hindered.
You can use sensitivity labels from the MIP framework to:
- Enforce protection settings like encryption or watermarks on labeled content
- Protect Microsoft 365 content across platforms and devices
- Extend sensitivity labels to protect content in third-party apps and services
- Protect containers that include Teams, Microsoft 365 groups, and SharePoint sites (requires an Entra ID Premium P1 license)
Up until recently, it was only possible to apply sensitivity labels to emails or documents. Last year, Microsoft introduced the ability to use sensitivity labeling to classify and protect containers.
Using sensitivity labels to protect sensitive content in Microsoft Teams sites, Microsoft 365 groups, and SharePoint sites
Now, in addition to using sensitivity labels to classify and protect documents and emails, you can also use sensitivity labeling to protect content in the following containers:
- Microsoft Teams sites
- Microsoft 365 groups
- SharePoint Online sites
When you apply a sensitivity label to a supported container, the label automatically applies the classification and configured protection settings to the site or group.
For this container-level classification and protection, you can use the following label settings:
- Privacy (public or private) of team sites and Microsoft 365 groups
- External user access
- Access from unmanaged devices
- External sharing from SharePoint sites (in preview)
For example, you can create a sensitivity label for confidential information (maybe called "Confidential") that, when applied during site or group creation, only allows users to create a site/group with a specific privacy setting—in this case, you'd probably want it to be private. Additionally, you might want to prevent external user access so that owners are prevented from adding people outside your organization.
Good to know:
- Content in these containers does not inherit the labels for the classification or settings for files and emails, such as visual markings and encryption. You need to make sure you've enabled sensitivity labels for Office files in SharePoint and OneDrive if you want users to be able to label their individual documents in SharePoint sites or team sites.
- Because this feature uses Entra ID functionality, your organization needs to have at least one active subscription to Microsoft Entra ID P1 (formerly known as Azure Active Directory Premium P1). You can read more about Information Protection licensing requirements in the official Microsoft documentation.
- You need to enable sensitivity labels for containers (it's turned off by default) and synchronize your sensitivity labels to Entra ID by connecting to Security & Compliance Center PowerShell.
- Once you've published your sensitivity labels, users will have the option to set a sensitivity label when creating a new group, team, or site. Note that users are only given the option to add a sensitivity label when creating a Microsoft 365 group via specific supported workloads—namely, SharePoint, Microsoft Teams, Outlook (on the web and for Windows, macOS, iOS, and Android), Forms, Stream, and Planner.
- Microsoft recommends not changing the site and group settings for a sensitivity label after the label has been applied to teams, groups, or sites. If you do, remember that it will take 24 hours for the changes to be applied to all containers that have the label.
Sensitivity labels applied at the container level serve a different purpose than sensitivity labeling for documents and emails—despite sharing a name and the ability to include settings for both scopes ("Files & emails" and "Groups & sites") in the same sensitivity label.
Essentially, what makes them different is the level at which you apply them (defining the scope) and the additional licensing requirements to enable labeling at the group and site levels. The fact is, the two scopes of sensitivity labelling are complementary; to really ensure your organizational data stays secure, it's a good idea to use a combination of tactics.
Sensitivity labels in Microsoft Teams
As you're probably aware by now, Microsoft Teams is closely tied to Microsoft 365 Groups and SharePoint Online team sites. So, if you've published sensitivity labels that have site and group settings enabled, those labels can also be applied to a team in Microsoft Teams.
Sensitivity labels function the same way in Teams as they do in SharePoint and Microsoft 365 Groups: depending on the label settings you've defined, a label will automatically apply changes to the team's privacy, guest access, and access from unmanaged devices (the ability to control external sharing from SharePoint sites is currently in preview).
Once you've published sensitivity labels with "Groups & sites" settings enabled, users will be able to select from a list of those sensitivity labels when creating a new team in Microsoft Teams.
In the example below, the user chose the "Confidential" label we discussed above—which automatically eliminates the option to make this team public:
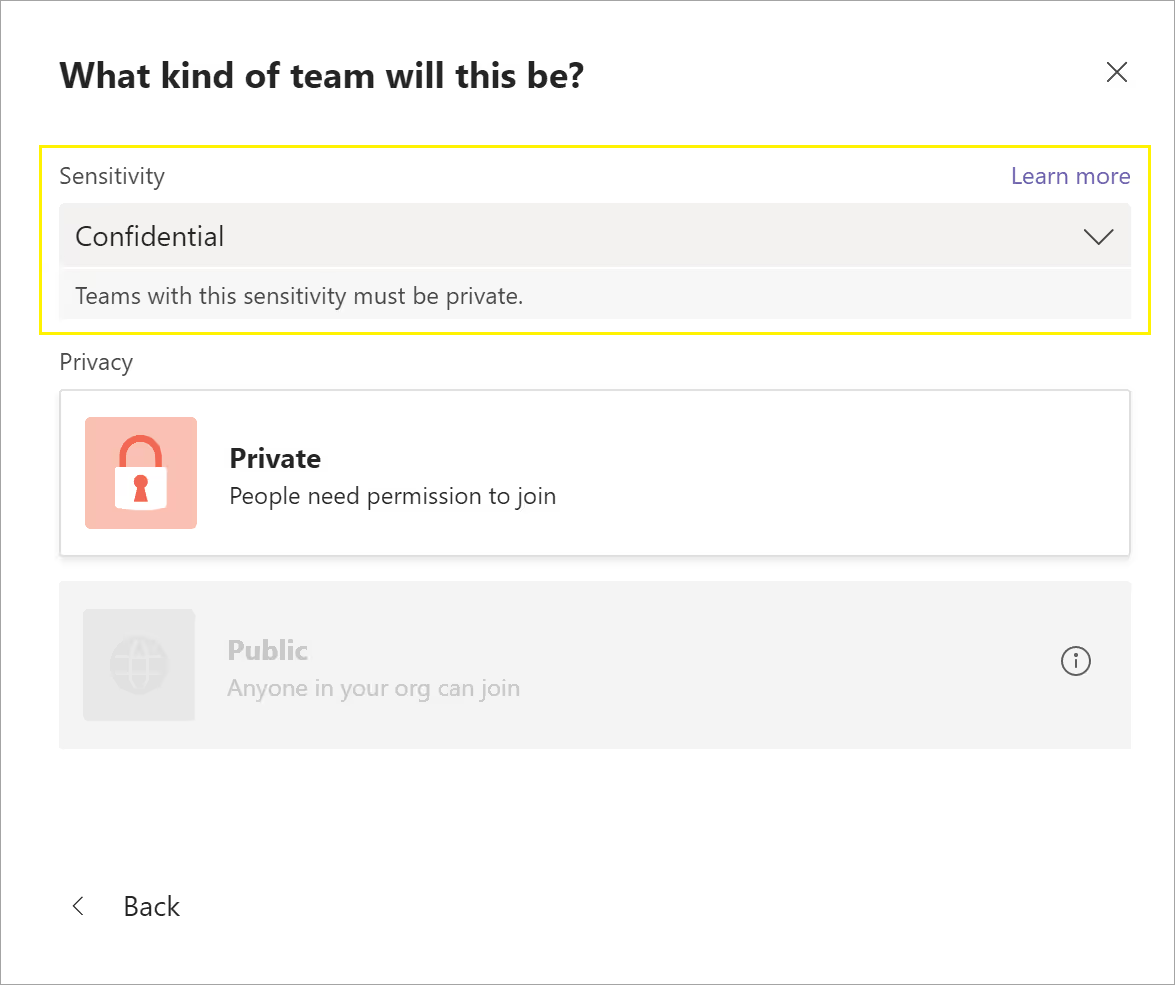
Source: https://docs.microsoft.com/en-us/microsoftteams/sensitivity-labels
By default, users are not required to select a sensitivity label. If users are creating tons of new teams in a hurry, they might choose to skip this step, in which case you'll need to manually check for teams missing labels and follow up with those owners later.
Note: When publishing your sensitivity labels, you can choose to configure the corresponding label policy so that users are required to apply a sensitivity label when creating new groups or sites (and by extension, creating new teams). Head to the official Microsoft documentation to find more information on what label policies can do.
Once the team is created, the chosen sensitivity label then appears in the upper-right corner of all the team's channels:
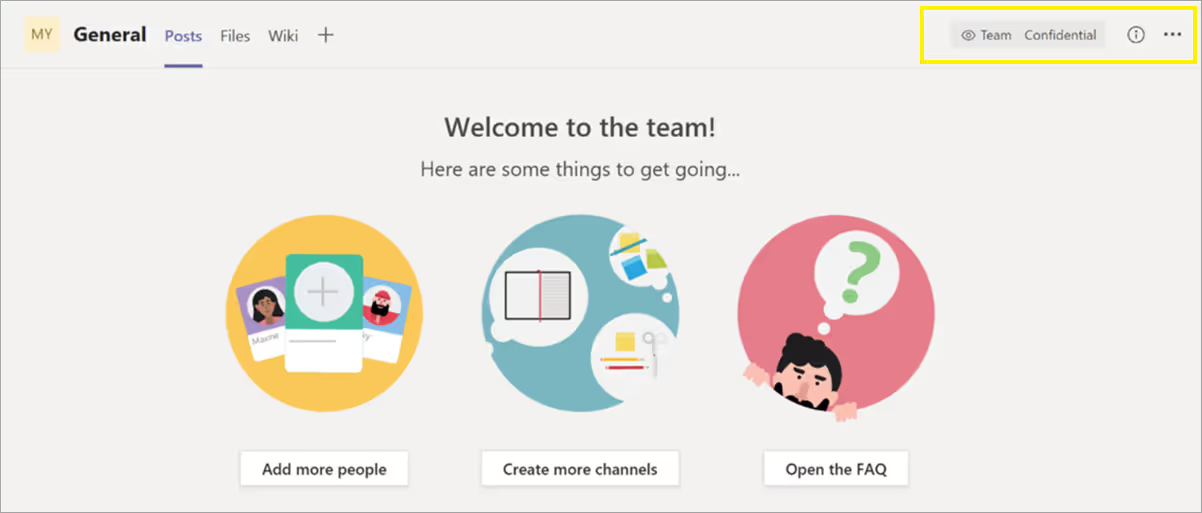
Source: https://docs.microsoft.com/en-us/microsoftteams/sensitivity-labels
The service automatically applies the same sensitivity label to the associated Microsoft 365 group and the connected SharePoint team site, as well.
Because the "Confidential" label settings don't allow guest access, this team will only be available to users in your organization. People outside your organization can't be added to the team.
Owners can change (or remove, depending on how your label policy is configured) the sensitivity label of their team at any time within the Microsoft Teams interface. In this example, if the owner later removed the "Confidential" label, the privacy settings of the team could then be changed to public and guest users could be invited to join the team. As an IT admin, you can also set or edit team sensitivity labels in the Microsoft Teams admin center.
When applying a more restrictive sensitivity label to an existing team, it's important to note that existing guests will not automatically be removed as team members when a label setting is changed to disallow guest access—the setting will only apply to new guest access moving forward. If you're starting to apply sensitivity labels to teams with existing guests, this is something to watch out for.
Good to know:
- Currently, users are not able to apply sensitivity labels to Teams created directly via Microsoft Graph APIs, PowerShell cmdlets, or provisioning templates at the time of creation. Sensitivity labels can be applied after creation via supported methods.
- Changes made to sensitivity labels outside the Teams app (i.e., by an IT admin) can take up to 24 hours to reflect in the Teams app. Additionally, any changes to a label made directly to a team's associated group or SharePoint site collection can take up to 24 hours to propagate to the Teams app.
Using sensitivity labels with Teams enables IT admins to regulate access to sensitive organization content created during collaboration within teams and also allows you to set different security settings based on each team's level of sensitivity. It's a great feature for organizations with Entra ID premium licensing that are just moving into Microsoft Teams.
However, if your organization has been using Teams or Microsoft 365 Groups for a while, then you might find yourself frustrated with the amount of manual work involved in assigning labels to all your existing groups and teams—especially if you're not a fan of PowerShell.
Not only that, but as an IT admin, you're probably not the best person to determine the sensitivity level of every single team—you're going to have to reach out to each team's owner and either ask them to assign a label to their team in the Teams app or relay that information back to you. And if you ask them to assign a label themselves, what are the chances that everyone will actually follow through?
Secure Microsoft Teams with sensitivity tags in ShareGate
What if you want to apply custom security settings to each of your teams without having to jump through all those hoops?
ShareGate, our Microsoft 365 management solution, has a sensitivity tag feature that enables you to automatically apply custom security settings to your teams and Microsoft 365 groups depending on each one's level of sensitivity.
You can manage a Microsoft 365 group or team's individual security settings directly in-app, giving you more granular control over each team's security settings—and without the need for an Entra ID Premium license.
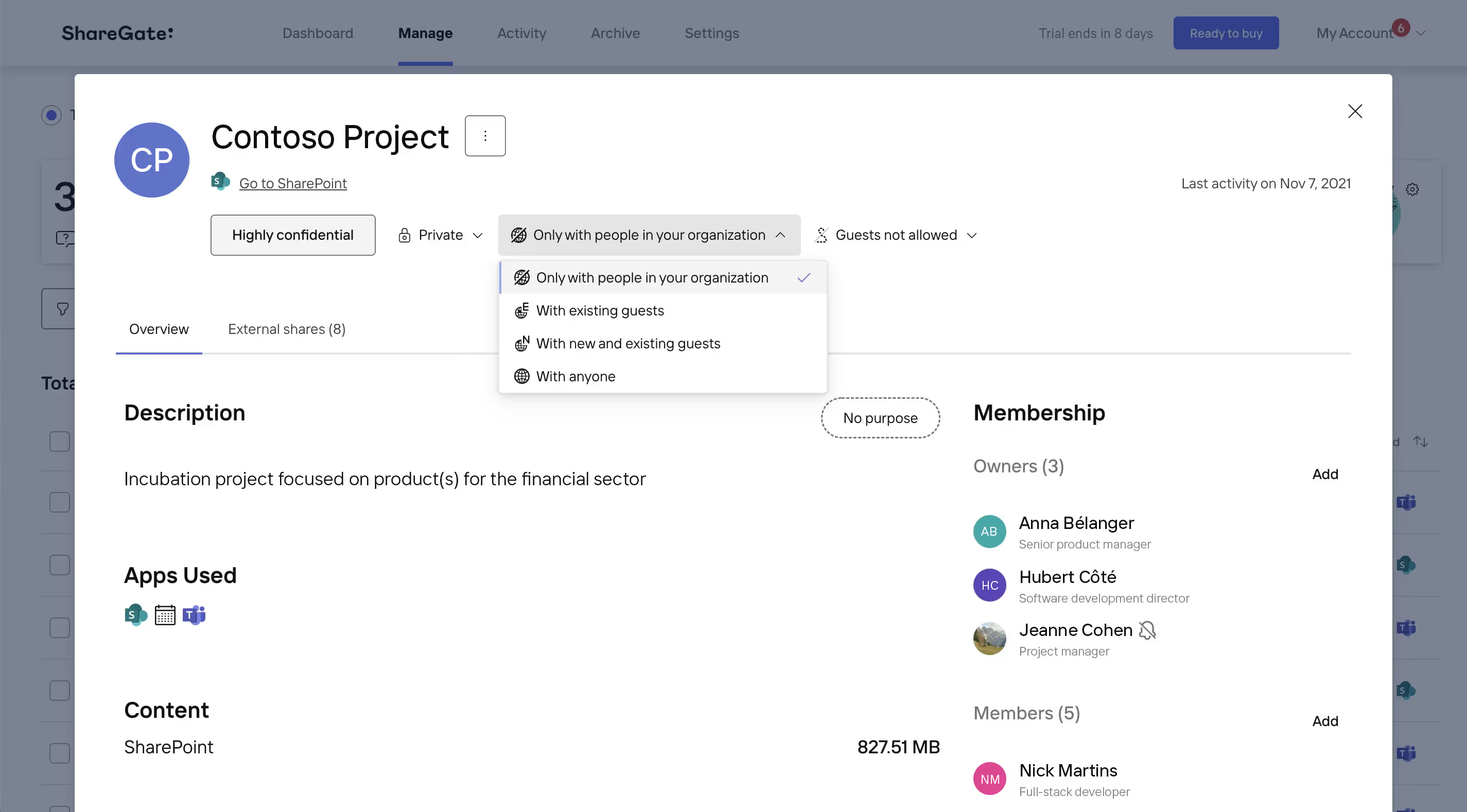
Edit security settings at the group/team level.
ShareGate enables you to manage the following security settings at the team level:
- Privacy status: Set to "Public" or "Private"
- External sharing: Set to "Anyone", "New and existing guests", "Existing guests", or "Only people in your organization"
- Guest access: Set to "Guests allowed" or "Guests not allowed"
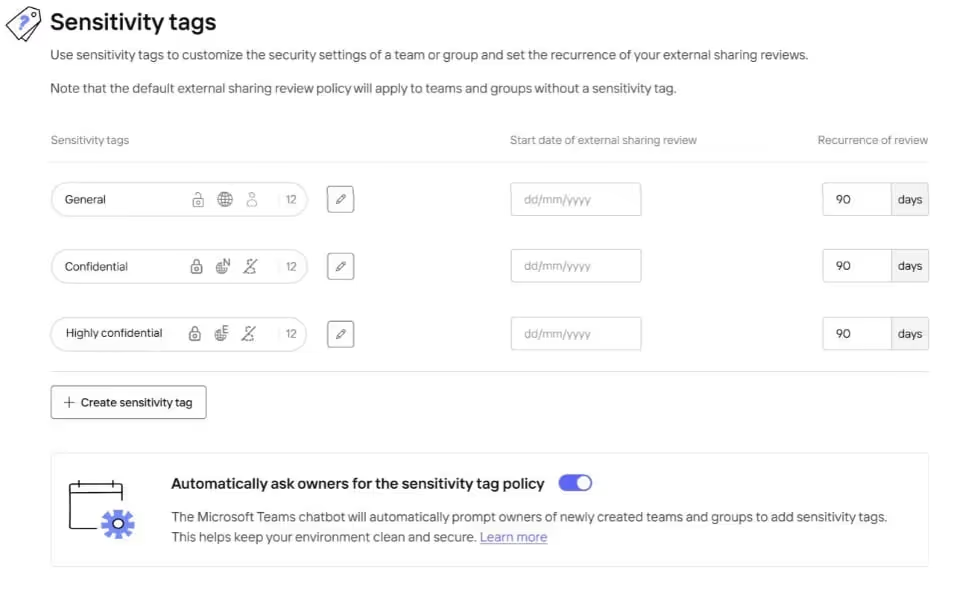
To make things easier and apply the correct security settings automatically, you can create your own sensitivity tags in ShareGate with customized privacy status, external sharing, and guest access settings.
To help you get started, you can choose from the following default sensitivity tags, which you can modify or even delete:
- General: Sets the group/team to public, allows external sharing with anyone and enables guest access
- Confidential: Sets the group/team to private, only allows external sharing with new and existing guests, and disables guest access
- Highly confidential: Sets the group/team to private and disables external sharing and guest access
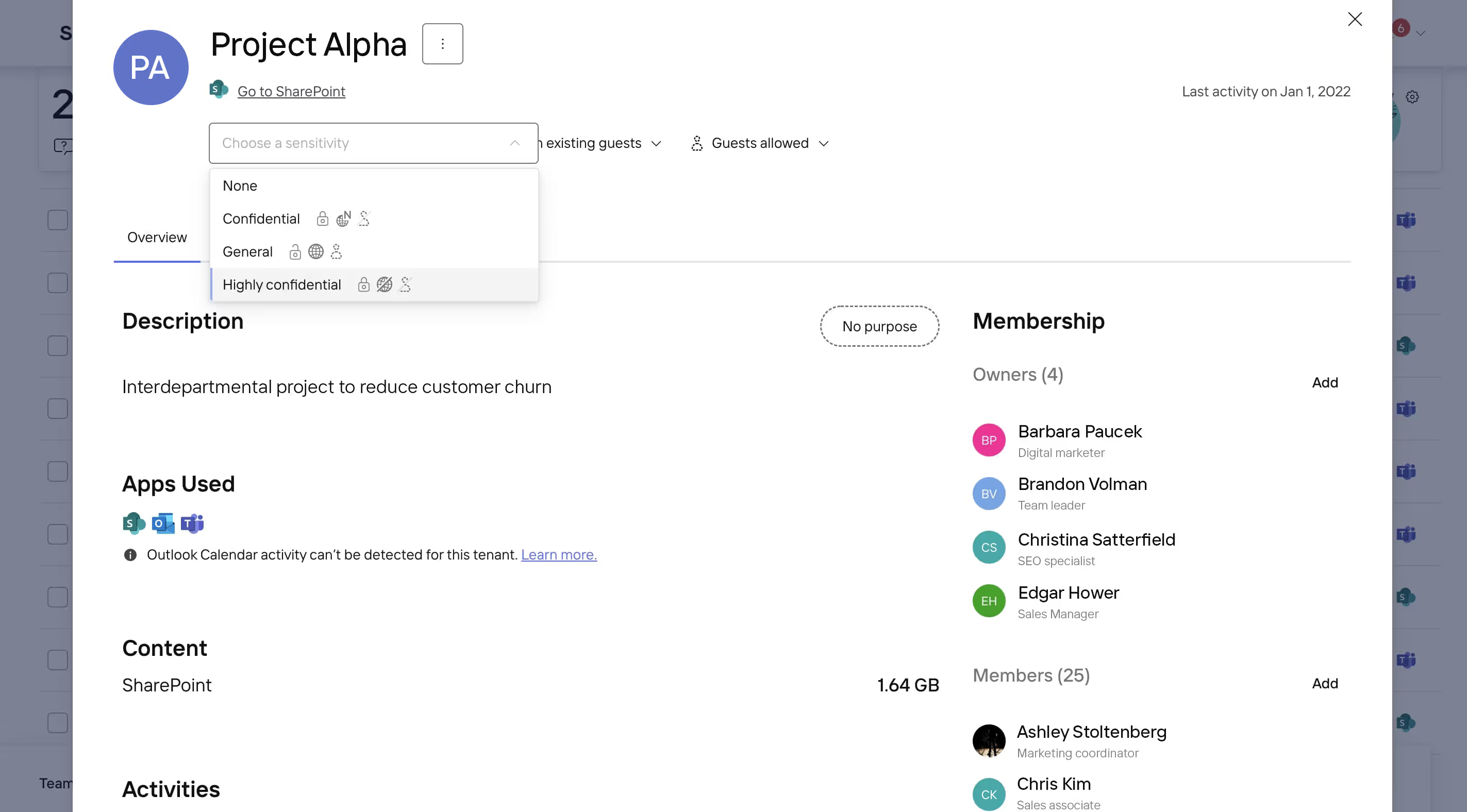
Create and edit group sensitivity labels in-app.
If you choose to create your own custom sensitivity tags, be sure to also include a detailed description that clearly defines the corresponding group sensitivity level for users creating a new team (more on that in a minute!).
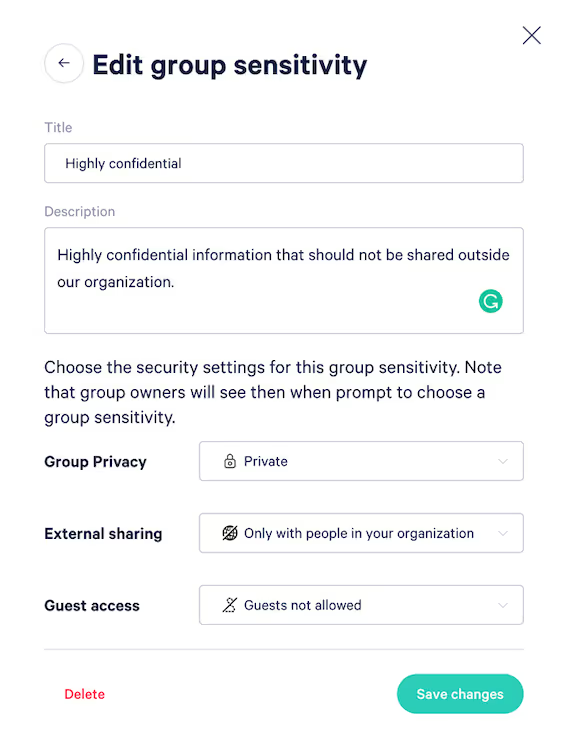
Add a description to help owners select the correct security settings.
Once you've defined your sensitivity tags, you can manually add labels to a team or overwrite a selection made earlier by an owner.
Sounds great! But how is our group sensitivity tag feature different from Microsoft's container-level security labeling?
Apply sensitivity tags to automatically control security settings at the team level
If your organization already has a ton of existing teams, then micromanaging the security settings of each team can still be a lot of time-consuming work for IT—especially if you're not in a position to know the sensitivity level of every single team.
Never fear! ShareGate's chatbot for Microsoft Teams is here!
In combination with "Group purpose"—our feature that helps you understand why owners create their teams—our conversational chatbot collects this information from owners directly in their flow of work in Microsoft Teams.
Shortly after an owner creates a new Microsoft 365 group—whether they do so by creating a new team in Microsoft Teams or via any of the other 19 ways to create a Microsoft 365 group—our chatbot will reach out to ask them for the group’s reason of creation and level of sensitivity.
The bot will present them with the options you’ve pre-populated as well as each one’s description, making it easy for owners to make an educated decision.
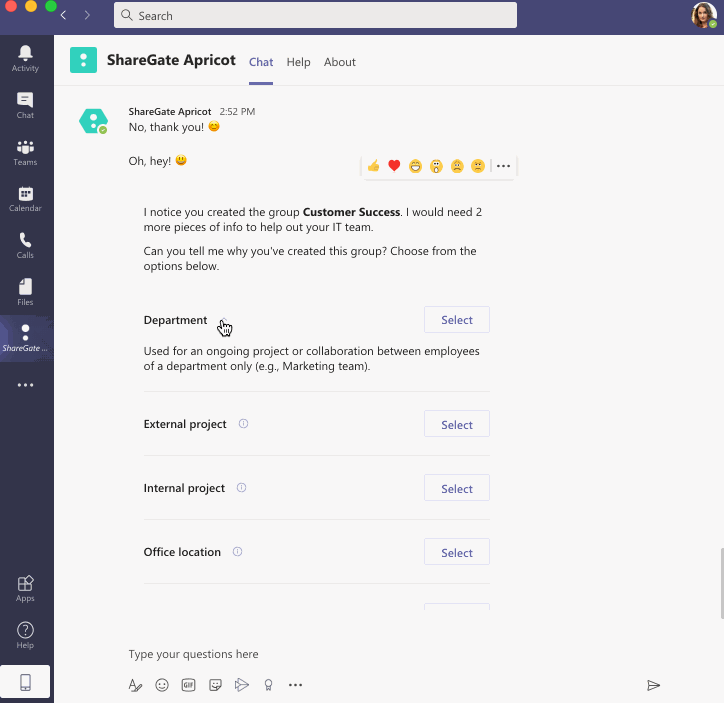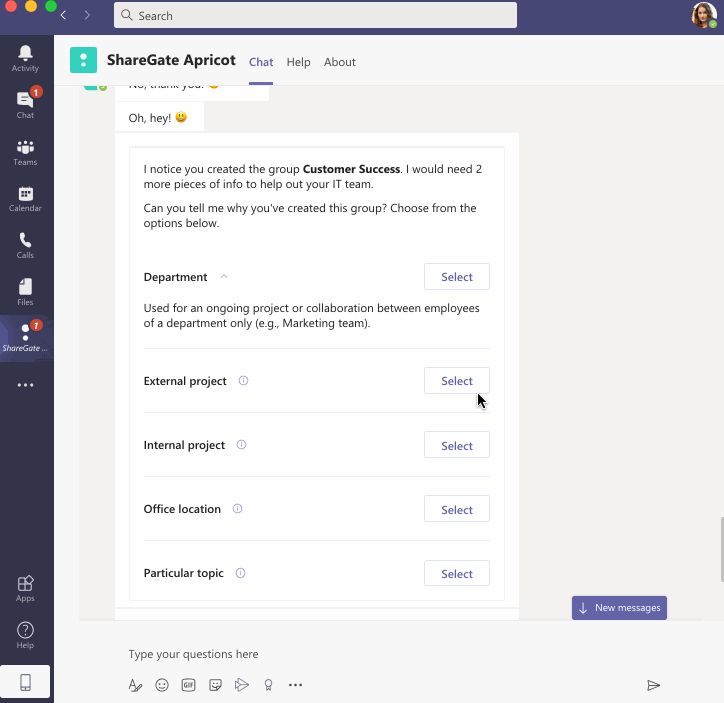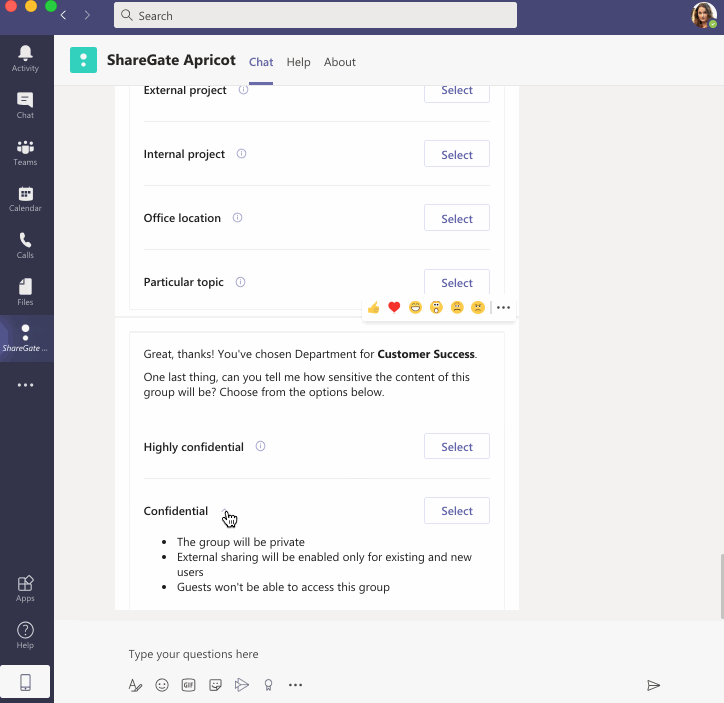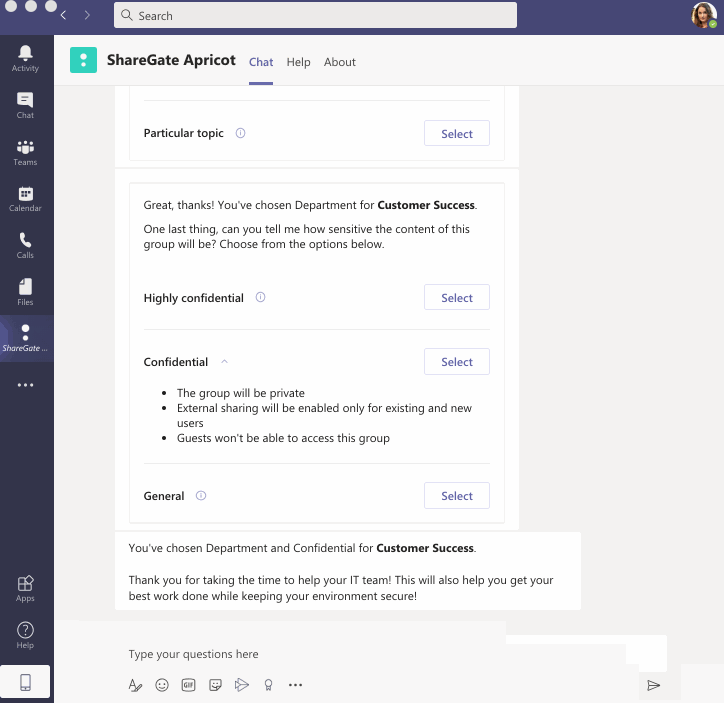
Owners pick the purpose and group sensitivity label that best fits their team.
You’ll now also be able to assess how much of a security risk that team poses to your business. But more importantly, once the owner has selected a sensitivity tag, the corresponding security settings will automatically be applied to their group/team.
That way, you can rest easy knowing that the appropriate controls have been applied from the moment the team is created.
Want owners to only assign a purpose OR a sensitivity tag and not both? You can do that easily now that we’ve split up the policies.
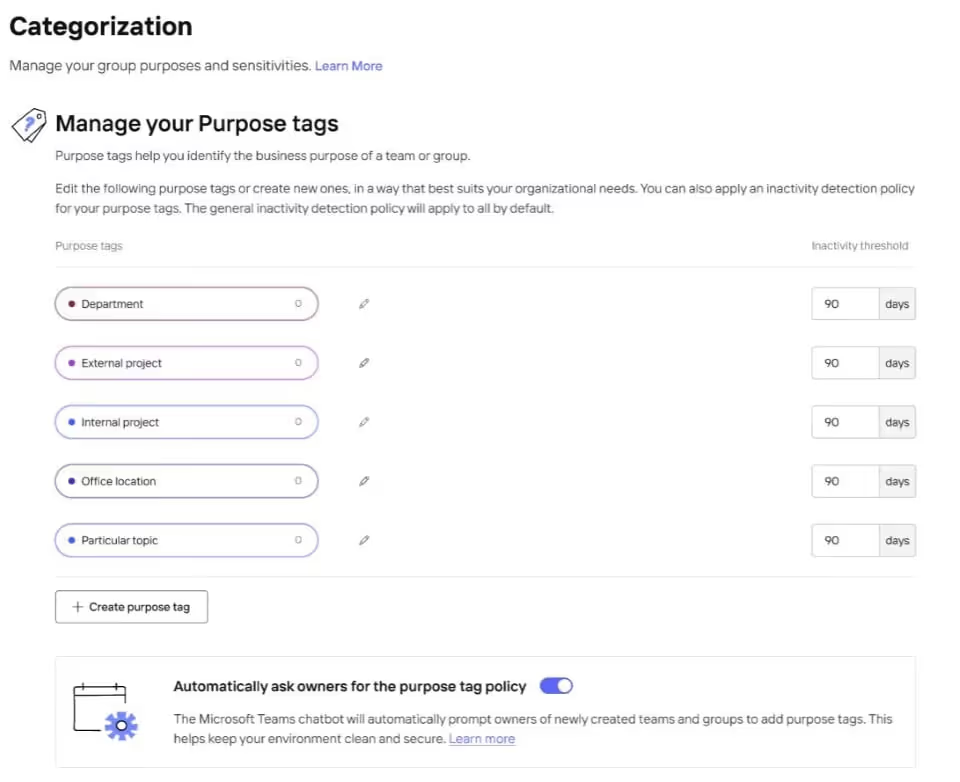
Simply go to Categorization in Policies and toggle on the automation for the policy you want.
- Purpose tag to identify the business purpose of a team/group
- Sensitivity tag to identify the sensitivity level of the team/group, and automatically apply the right security settings to it
Detect and correct sensitivity mismatches to enforce your security settings
Remember when we told you that owners can change a Microsoft 365 sensitivity label after it's been applied to a site, group, or team? This can pose a security risk to your organizational data if you don't catch a potentially harmful change in time.
ShareGate helps mitigate this risk by flagging sensitivity mismatches for you!
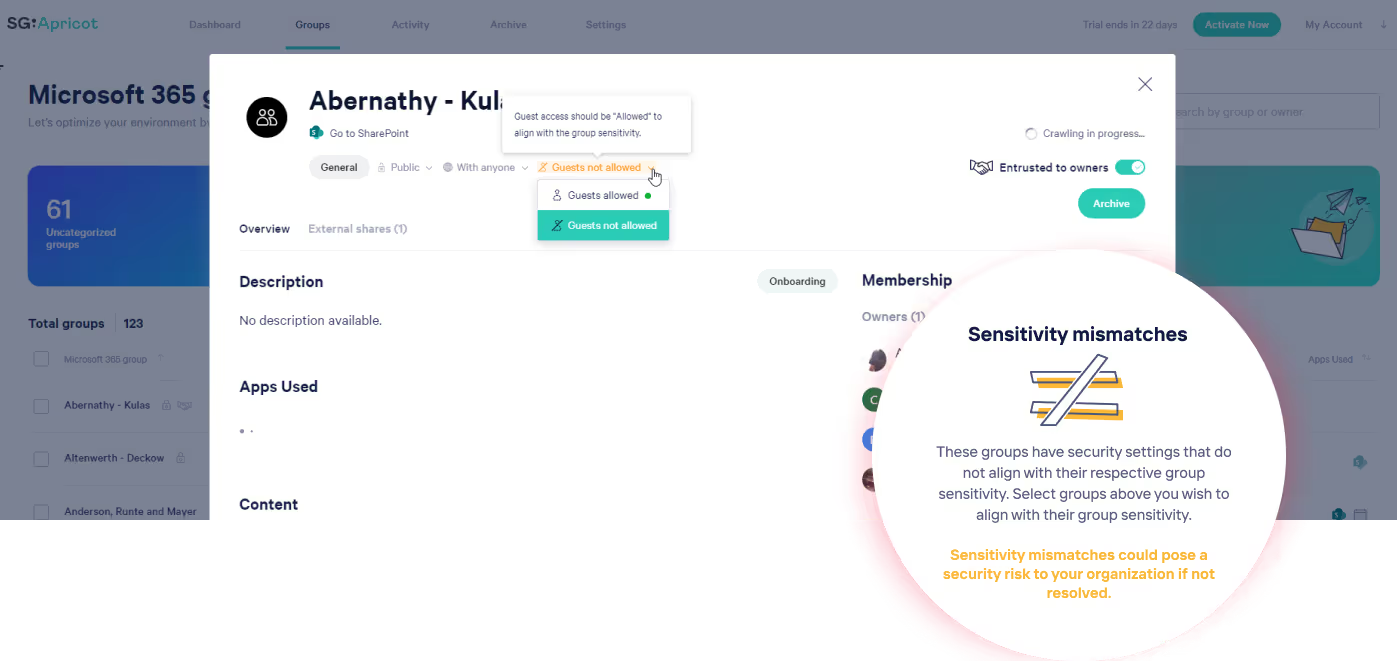
See potential security flaws so you can manually correct them.
Unlike sensitivity labels in Teams, owners can't change a ShareGate sensitivity tag once it's been set. So, if an owner proceeds to change any of their team's security settings after the sensitivity tag's corresponding settings have been automatically applied—i.e., they labeled their team as "Confidential" and later changed the privacy status from private to public—ShareGate identifies the mismatch for you.
And unlike container-level sensitivity labels in Microsoft 365, when you change a team's guest access settings in ShareGate to be more restrictive, all existing guests are automatically removed from the team.
Changes to a team's sensitivity tag or security settings in ShareGate are applied right away—you don't need to wait 24 hours for changes to take effect. So, you can spot potential security flaws in your environment and quickly correct the situation to avoid having your data fall into the wrong hands.
If your organization uses MIP sensitivity labels for documents and emails (with settings defined at the "Files & emails" scope in the sensitivity labeling wizard), you can use those capabilities in tandem with ShareGate's sensitivity tag feature.
As we mentioned for MIP container-level sensitivity labels above, the two scopes of labeling are complementary; depending on the needs of your organization, you may want to use ShareGate's sensitivity tags at the container level and MIP sensitivity labels for documents and emails together for maximum data protection.
MIP sensitivity labels and ShareGate sensitivity tags: Feature comparison table
Before you go, we know there's a lot of information to parse through in the article above. We created this handy table to help you visualize the different functionalities that are available in the context of container-level sensitivity labeling.
ShareGate is easy to setup and even easier to manage—no clunky interface, no coding, and no Entra ID premium subscription required.
From SharePoint migration and content management to ongoing Microsoft Teams governance, ShareGate gives you everything you need to achieve successful Microsoft 365 deployment and adoption. Learn what's included and how to get more from a ShareGate subscription.
If you’re ready to start categorizing your groups and teams according to business purpose, take a look at our documentation to learn how to set it up!


.svg)
%20(1).avif)











.avif)
.avif)